I am trying to acquire access token on behalf of a user(client application). So I am generating an accesss token for a client application which it be using to access middle tier service. The middle tier service will be accessing the downstream service. Basically the client needs to access the downstream service but it can't use the service directly, so middle tier service will be accessing on behalf of the client. I am getting the following error :
error message: 'AADSTS70000: The request was denied because one or more scopes requested are unauthorized or expired. The user must first sign in and grant the client application access to the requested scope.
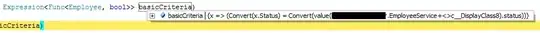
The code I have written is :
string[] targetScopes = new string[] { "api://xxxx-xxxx-xxxx-xxxx/Downstreamservice.ReadWrite" };
UserAssertion userAssertion = new UserAssertion(middleTierServiceAccessToken);
string clientId = configuration["Auth:ClientId"];
string redirectUri = url;
string authority = string.Format(CultureInfo.InvariantCulture, configuration["Auth:AzureAdInstance"], configuration["Auth:Tenant"]);
string clientSecret = "xxx-xxxx-xxxx";
// Initialize the confidential client application
IConfidentialClientApplication app = ConfidentialClientApplicationBuilder
.Create(clientId)
.WithRedirectUri(redirectUri)
.WithAuthority(new Uri(authority))
.WithClientSecret(clientSecret)
.Build();
// Exception with the above error is getting thrown in the line below
AuthenticationResult result = await app.AcquireTokenOnBehalfOf(targetScopes, userAssertion).ExecuteAsync();
string downStreamServiceAccessToken = result.AccessToken;
The middleTierServiceAccessToken is being fetched correctly.Do i need to add any scope on the client side ?
I have checked repeatedly the targetscope url and if the client id of my middletierService is added as authorized client application. But I am still getting the error. I have tried switching the cases of the scope to downstreamservice.readwrite but that did not work either.
i can't figure out the reason why this is happening.