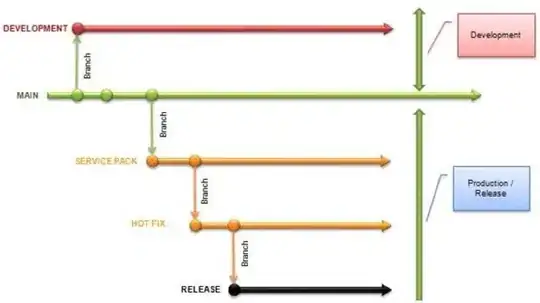
In your screenshot, you are using Oauth 1.0 which you need to set resource and this makes you can't set API scope inside the authorization, you need to use OAuth 2.0. By the way, client credential flow will make the scope set to xxx/.default, this flow won't contain scope name as well, so you can't use client credential flow as well.
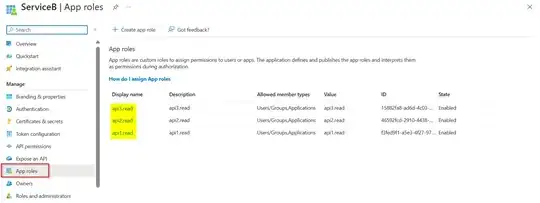
I have a sample here. Firstly, here's the settings in Service-B. I integrated Azure AD into my web api project.
builder.Services.AddMicrosoftIdentityWebApiAuthentication(builder.Configuration);
"AzureAd": {
"Instance": "https://login.microsoftonline.com/",
"ClientId": "client_id",
"ClientSecret": "client_secret",
"Domain": "tenant_id",
"TenantId": "tenant_id"
},
Then in my web api:
[ApiController]
[Route("[controller]")]
[Authorize]
public class WeatherForecastController : ControllerBase
{
public WeatherForecastController(){}
[RequiredScope("Tiny.Read1")]
[HttpGet]
public async Task<string> GetAsync()
{
return "world";
}
[HttpGet("greet")]
[RequiredScope("Tiny.Read")]
public string greet() {
return "hello";
}
}
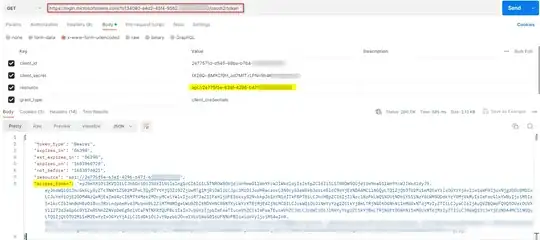
I used auth code flow to generate an access token which containing the scope I defined:
Then here's my test result:
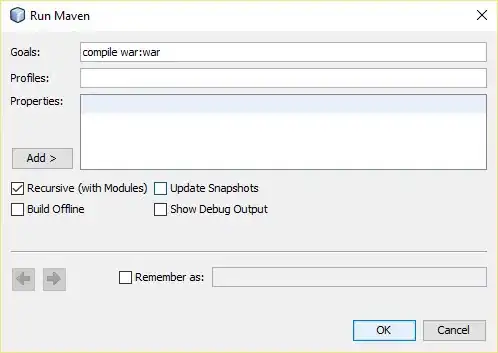
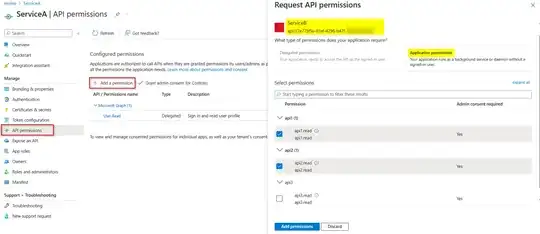
About how to expose custom API scope, you can follow this official document. This answer showed how to generate access token by auth code flow. But if you are trying to generate access token in Service-A to call Service-B, you may use on_behalf_flow, this answer contained code snippet with Microsoft identity and use _tokenAcquisition to generate access token, and this answer is for a client call AAD protected API.