To clarify, my specific confusion is centered around the fact that all instructions in a PE executable are written assuming the base image address is = 00400000. However, when debugging an executable, the addresses used adapt to whatever base image address is decided at runtime.
I have opened a simple process at a base image different from the default:
 Then ran a debugger and took note of the call of a simple function:
Then ran a debugger and took note of the call of a simple function:
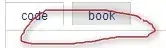 The call is to a pointer that has a B0F4 offset from the base image address (930000 + B0F4). The B0F4 pointer being the IAT to the dll containing the function being used.
The call is to a pointer that has a B0F4 offset from the base image address (930000 + B0F4). The B0F4 pointer being the IAT to the dll containing the function being used.
My confusion is, how is the instruction calling that particular address, which uses 930000 as a base address. This base address is decided at runtime.
When looking at that same instruction inside the PE file, the same call is made, but the default address is used.
 The B0F4 offset is applied to 00400000.
The B0F4 offset is applied to 00400000.
How does windows do this. Is there a hardware solution to this? Some sort of instruction that decides that all further instructions operate with an offset? Or, as ridiculous as that sounds, does the os somehow identify all addresses used and changes them based on the new image base