We have an auto-scaling group which spins up multiple instances as required. All instances in auto-scaling group take their data from separate EC2 instance (running NFS) so they can all share the same data.
Following are the settings for NFS server which allows everyone access to it via wildcard
/var/nfs *(rw,sync,no_root_squash,no_subtree_check)
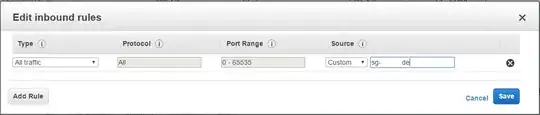
Now, when server auto-scales it assigns it's own private/public IP address randomly to EC2 instances running under auto-scaling group, now I have to assign these private/public IP addresses to NFS instance security group like this
Or else I have security weak option to allow all traffic on all port from any source, ie: security group with all access to all ports from all sources which would be disaster.
Without these 2 options my EC2 instances running under auto-scaling group does not connect to NFS instance.
I have tried many options like allow all traffic from all port to auto-scaling security group ‘Group ID’ OR allow all traffic from all port to default security group ‘Group ID’ like this
But none of this works and I have been in weird situation!
PS: There is no port issue since I have been trying with all tarffic.