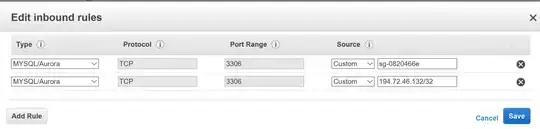
In AWS, our auto scaling group is launching new instances in different availability zones (for high availability) and these web instances of course require access to database (RDS) service on port 3306.
Now, what IP addresses should I allow in my RDS security group for port 3306?
Since each newly launched instance has different IP address each time so how can we add them into security group?
BTW: This is not just the issue for RDS security grouo but for all security groups as I can't restrict them.