I am using C# to create new computer accounts. My goal is to allow IT helpdesk personnel to add computers to the domain safely in the right OU. The way I intended to do this was to have them use a tool that would take the relevant information and create the account in Active Directory. So far, this all works great. There is only one snag - I can't figure out how to grant my workers the rights to join the computer to the domain. Normally in Active Directory you could change the group that is allowed to join the new computer to the domain. I am using DirectoryServices.AccountManagement and I cannot figure out how to do the same in code.
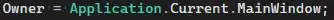
Here is my code:
PrincipalContext oPrincipalContext = GetPrincipalContext(sOU);
//The password is just a random construction.
//The computer SAM Account Name must end with a dollar sign in order for it
//to be usable.
ComputerPrincipal oComputerPrincipal = new ComputerPrincipal(oPrincipalContext,
sComputerName + "$",
RandomPassword(),
true);
//You actually need to save the record before it is actually created
oComputerPrincipal.Save();
This creates the computer accounts and puts them in the correct OU. However, you still need to be granted the rights to add a computer to the domain in order to hook a computer up to this account. I can't find the code to do so.
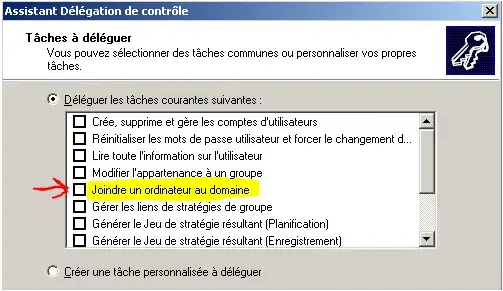
As a side note, I understand that I could grant my helpdesk personnel the permission to join computers to the domain. The problem, though, is that they would be able to do so without using this tool. They wouldn't realize that when they do that, they are sending the computers to the wrong OUs.
Update
Here is an updated picture to show you what I am trying to accomplish in code. As you can see in the image below, I am attempting to change the bottom box (via code) when I create a new computer account in code. See how it allows you to specify who can add this specific computer to the domain?