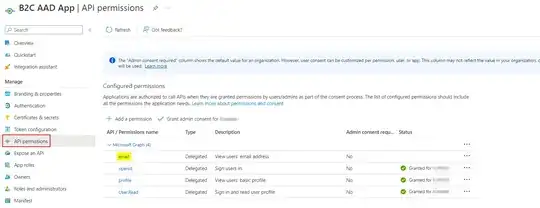
I registered one application in Azure AD tenant and added same API permissions as below:
In Token configuration, I added same optional claims for ID token like this:
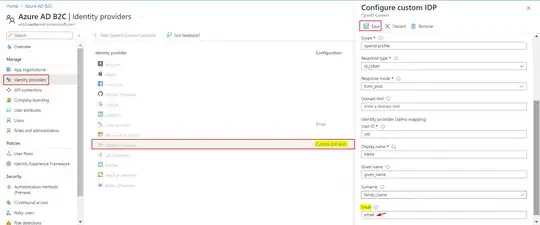
Now, I configured Azure AD as an identity provider in B2C tenant by adding custom IDP with below parameters:
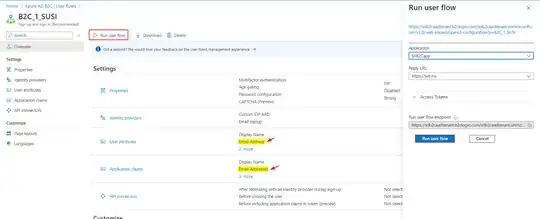
While running Sign Up and Sign In user flow, make sure to include email addresses claim like this:
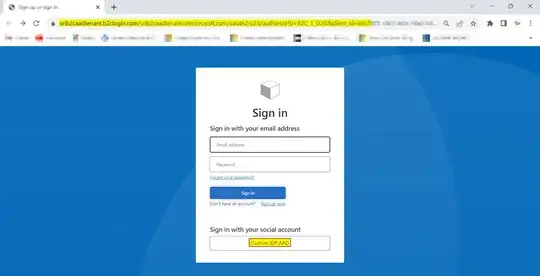
When I ran the user flow, I got below login screen with Custom IDP AAD button:
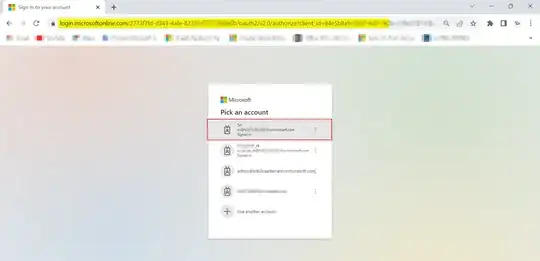
After clicking Custom IDP AAD button, I got below screen to pick account where I selected Sri account:
In my case, I got below screen after completing authentication process with claims from Azure AD:
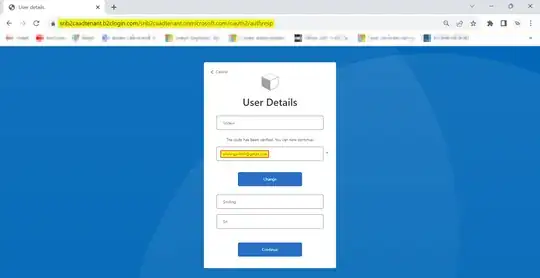
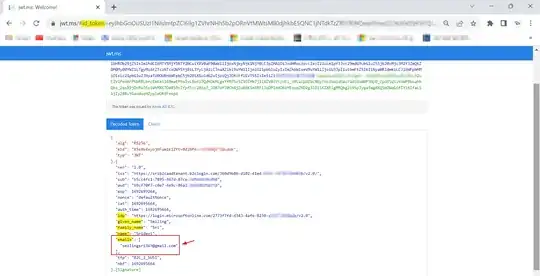
When I selected Continue, I got id_token with emails claim successfully like below:
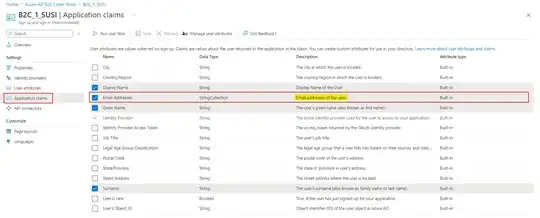
In your case, make sure to select Email addresses in Application claims of user flow to get email in id_token:
You need to add email as value while configuring Custom IDP for email field.
References:
Set up sign-in for an Azure AD organization - Azure AD B2C | Microsoft
Azure AD B2C "email" claim is missing from JWT - Stack Overflow by Carl Zhao