I created an Azure AD Application and granted API permissions:
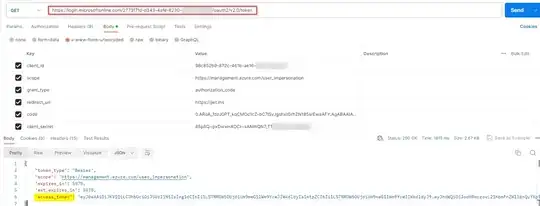
I generated access token by using below parameters:
https://login.microsoftonline.com/TenantID/oauth2/v2.0/token
client_id:ClientID
scope:https://management.azure.com/user_impersonation
grant_type:authorization_code
redirect_uri:https://jwt.ms
code:code
client_secret:ClientSecret
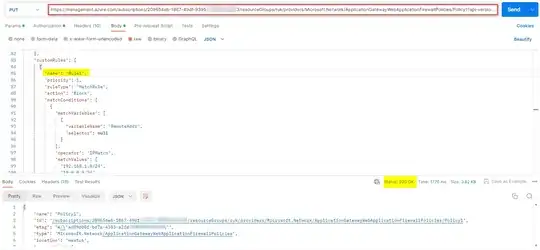
By using the access token, I created Web Application Firewall Policies:
PUT https://management.azure.com/subscriptions/SubID/resourceGroups/ruk/providers/Microsoft.Network/ApplicationGatewayWebApplicationFirewallPolicies/Policy1?api-version=2023-02-01
{
"location": "WestUs",
"properties": {
"policySettings": {
"logScrubbing": {
"state": "Enabled",
"scrubbingRules": [
{
"state": "Enabled",
"matchVariable": "RequestArgNames",
"selectorMatchOperator": "Equals",
"selector": "test"
},
{
"state": "Enabled",
"matchVariable": "RequestIPAddress",
"selectorMatchOperator": "EqualsAny"
}
]
}
},
"managedRules": {
"managedRuleSets": [
{
"ruleSetType": "OWASP",
"ruleSetVersion": "3.2",
"ruleGroupOverrides": [
{
"ruleGroupName": "REQUEST-931-APPLICATION-ATTACK-RFI",
"rules": [
{
"ruleId": "931120",
"state": "Enabled",
"action": "Log"
},
{
"ruleId": "931130",
"state": "Disabled",
"action": "AnomalyScoring"
}
]
}
]
}
],
"exclusions": [
{
"matchVariable": "RequestArgNames",
"selectorMatchOperator": "StartsWith",
"selector": "hello",
"exclusionManagedRuleSets": [
{
"ruleSetType": "OWASP",
"ruleSetVersion": "3.2",
"ruleGroups": [
{
"ruleGroupName": "REQUEST-930-APPLICATION-ATTACK-LFI",
"rules": [
{
"ruleId": "930120"
}
]
},
{
"ruleGroupName": "REQUEST-932-APPLICATION-ATTACK-RCE"
}
]
}
]
},
{
"matchVariable": "RequestArgNames",
"selectorMatchOperator": "EndsWith",
"selector": "hello",
"exclusionManagedRuleSets": [
{
"ruleSetType": "OWASP",
"ruleSetVersion": "3.1",
"ruleGroups": []
}
]
},
{
"matchVariable": "RequestArgNames",
"selectorMatchOperator": "StartsWith",
"selector": "test"
},
{
"matchVariable": "RequestArgValues",
"selectorMatchOperator": "StartsWith",
"selector": "test"
}
]
},
"customRules": [
{
"name": "Rule1",
"priority": 1,
"ruleType": "MatchRule",
"action": "Block",
"matchConditions": [
{
"matchVariables": [
{
"variableName": "RemoteAddr",
"selector": null
}
],
"operator": "IPMatch",
"matchValues": [
"192.168.1.0/24",
"10.0.0.0/24"
]
}
]
},
{
"name": "Rule2",
"priority": 2,
"ruleType": "MatchRule",
"matchConditions": [
{
"matchVariables": [
{
"variableName": "RemoteAddr",
"selector": null
}
],
"operator": "IPMatch",
"matchValues": [
"192.168.1.0/24"
]
},
{
"matchVariables": [
{
"variableName": "RequestHeaders",
"selector": "UserAgent"
}
],
"operator": "Contains",
"matchValues": [
"Windows"
]
}
],
"action": "Block"
},
{
"name": "RateLimitRule3",
"priority": 3,
"rateLimitDuration": "OneMin",
"rateLimitThreshold": 10,
"ruleType": "RateLimitRule",
"matchConditions": [
{
"matchVariables": [
{
"variableName": "RemoteAddr",
"selector": null
}
],
"operator": "IPMatch",
"negationConditon": true,
"matchValues": [
"192.168.1.0/24",
"10.0.0.0/24"
]
}
],
"groupByUserSession": [
{
"groupByVariables": [
{
"variableName": "ClientAddr"
}
]
}
],
"action": "Block"
}
]
}
}
The WAF policy created in the resource group:
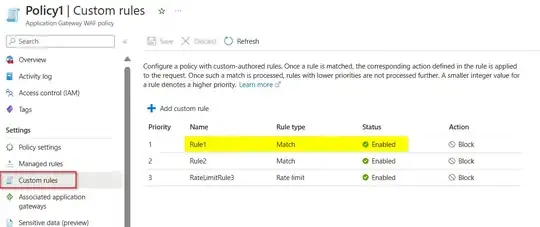
Now I tried to update the WAF policy, updating the custom rule name:
PUT https://management.azure.com/subscriptions/SubID/resourceGroups/ruk/providers/Microsoft.Network/ApplicationGatewayWebApplicationFirewallPolicies/Policy1?api-version=2023-02-01
"customRules": [
{
"name": "RuleRuk",
"priority": 1,
"ruleType": "MatchRule",
"action": "Block",
"matchConditions": [
{
"matchVariables": [
{
"variableName": "RemoteAddr",
"selector": null
}
],
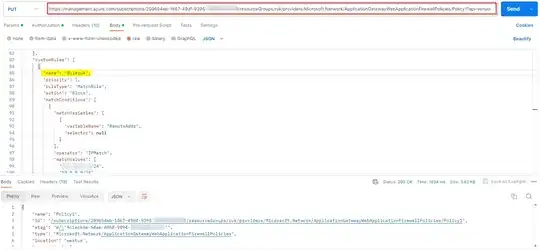
The custom rule name updated successfully like below:
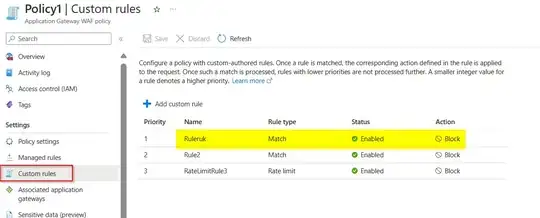
Note that: You have to pass resource group name in which the WAF policy is present to update the policy.





