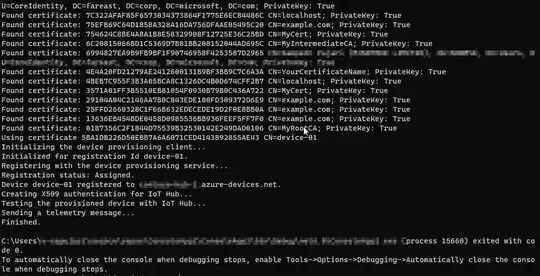
I try to set an Azure DPS with the authentication type "x509 CA certificate". Everything works except the IoT hub shows devices provisioned with DPS as "X509 self-signed" instead of "Certificate Authority".
With devices directly created on IoT Hub (NOT via DPS), authenticated types are set to Certificate Authority. This is the behavior I want to reproduce with devices created from DPS.
My DPS enrollment group settings:
For testing, I'm using the IoT-Sdk-CSharp and follow this sample.
Do you know what I have to change in DPS for my devices to appear with the "Certificate Authority" authentication type?
Thank you for your help. Have a nice day.