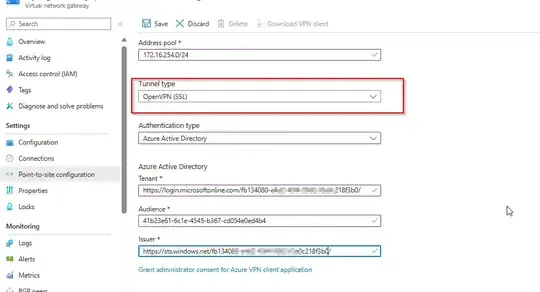
I'm trying to configure VPN Gateway to provide access to VNET in Azure. For this I used following documentation:
https://learn.microsoft.com/en-us/azure/vpn-gateway/create-routebased-vpn-gateway-cli
In the result I wrote following bash script for creating required services in Azure:
#!/bin/bash
set -e
eval $(grep -v -e '^#' .env | xargs -I {} echo export \'{}\')
az network vnet subnet create \
--vnet-name $VNET_NAME \
--name GatewaySubnet \
--resource-group $RESOURCE_GROUP_NAME \
--address-prefix "10.0.17.0/27"
az network public-ip create \
--name "${VNET_NAME}-vpn-ip" \
--resource-group $RESOURCE_GROUP_NAME \
--allocation-method Dynamic
az network vnet-gateway create \
--name $VNET_GETEWAY_NAME \
--location $VNET_LOCATION \
--public-ip-address "${VNET_NAME}-vpn-ip" \
--resource-group $RESOURCE_GROUP_NAME \
--vnet $VNET_NAME \
--gateway-type Vpn \
--sku VpnGw1 \
--vpn-type RouteBased \
--address-prefixes "172.16.201.0/24" \
--vpn-gateway-generation Generation1 \
--client-protocol OpenVPN \
--root-cert-name RootCert \
--root-cert-data caCert.pem \
--vpn-auth-type Certificate \
--no-wait
For generation of self-signed certificates I use strongSwan and openssl by documentation from following topics:
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-certificates-point-to-site-linux
Сorrectness of created certificates I checked by openssl verify util
Next step was Download VPN Client for OpenVPN
After that I filled in user and blocks in vpnconfig.ovpn
# P2S client certificate
# Please fill this field with a PEM formatted client certificate
# Alternatively, configure 'cert PATH_TO_CLIENT_CERT' to use input from a PEM certificate file. <cert>
# Content of userCert.pem or client-cert.pem files
</cert>
# P2S client certificate private key
# Please fill this field with a PEM formatted private key of the client certificate.
# Alternatively, configure 'key PATH_TO_CLIENT_KEY' to use input from a PEM key file.
<key>
# Content of userKey.pem or clientKey.pem files
</key>
For running OpenVPN connection I used Windows OpenVPN client. When used vpnconfig.ovpn to connect to Azure I get message error: Peer certificate verification failure.
OpenVPN logs
[Aug 4, 2023, 11:27:46] OpenVPN core 3.git::d3f8b18b win x86_64 64-bit built on Feb 7 2023 16:08:10
[Aug 4, 2023, 11:27:46] Frame=512/2048/512 mssfix-ctrl=1250
[Aug 4, 2023, 11:27:46] UNUSED OPTIONS 6 [resolv-retry] [infinite] 7 [nobind] 10 [persist-key] 11 [persist-tun] 15 [log] [openvpn.log] 16 [verb] [3]
[Aug 4, 2023, 11:27:46] EVENT: RESOLVE
[Aug 4, 2023, 11:27:46] EVENT: WAIT
[Aug 4, 2023, 11:27:46] WinCommandAgent: transmitting bypass route to 52.191.28.72 { "host" : "52.191.28.72", "ipv6" : false }
[Aug 4, 2023, 11:27:46] Connecting to [azuregateway-651a0077-6bec-43a5-9738-fb84b4090d03-55fa834d773d.vpn.azure.com]:443 (52.191.28.72) via TCPv4
[Aug 4, 2023, 11:27:46] EVENT: CONNECTING
[Aug 4, 2023, 11:27:46] Tunnel Options:V4,dev-type tun,link-mtu 1523,tun-mtu 1500,proto TCPv4_CLIENT,keydir 1,cipher AES-256-GCM,auth [null-digest],keysize 256,tls-auth,key-method 2,tls-client
[Aug 4, 2023, 11:27:46] Creds: UsernameEmpty/PasswordEmpty
[Aug 4, 2023, 11:27:46] Peer Info: IV_VER=3.git::d3f8b18b IV_PLAT=win IV_NCP=2 IV_TCPNL=1 IV_PROTO=30 IV_CIPHERS=AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305 IV_AUTO_SESS=1 IV_GUI_VER=OCWindows_3.3.7-2979 IV_SSO=webauth,openurl,crtext
[Aug 4, 2023, 11:27:47] Transport Error: OpenSSLContext::SSL::read_cleartext: BIO_read failed, cap=2576 status=-1: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed
[Aug 4, 2023, 11:27:47] EVENT: CERT_VERIFY_FAIL OpenSSLContext::SSL::read_cleartext: BIO_read failed, cap=2576 status=-1: error:1416F086:SSL routines:tls_process_server_certificate:certificate verify failed⏎[Aug 4, 2023, 11:27:47] EVENT: DISCONNECTED
Anybody have any thoughts how I can fix it?
I would be grateful for any advice!
I used 2 different ways to generate certificates (mentioned above) but no one give me the same result. I found similar issue but provided advices did not help to solve problem.
Azure VPN / OpenVPN(SSL) Peer certificate verification failure
In the result OpenVPN return the same message error: Peer certificate verification failure.