I am using devops pipeline to update a containerApp. The devops pipeline uses a self hosted agent pool which uses a VMSS agent. in the pipeline cli task i create a system assigned managed identity for the containerApp using az cli commands and in the next step i try to assign a registry ACR Pull role to the containerApp on a private ACR using the command below
az role assignment create \
--assignee-object-id $PRINCIPALID \
--assignee-principal-type ServicePrincipal \
--role AcrPull \
--scope /subscriptions/$(SUBSCRIPTION)/resourceGroups/$(RG_NAME)/providers/Microsoft.ContainerRegistry/registries/$(acrContainerName)
getting this error in devops console:
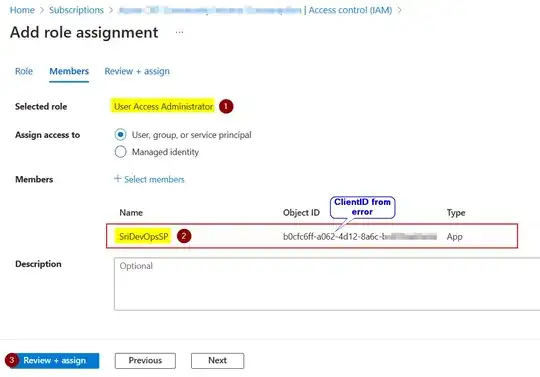
(AuthorizationFailed) The client '3447a78f-2d20-4a27-abcd-4050272e5946' with object id '3447a78f-2d20-4a27-abcd-4050272e5946' does not have authorization or an ABAC condition not fulfilled to perform action 'Microsoft.Authorization/roleAssignments/write' over scope '/subscriptions/12d3e9402-cddbf-4272-83b5-c479199032d6/resourceGroups/my-infra-rg/providers/Microsoft.ContainerRegistry/registries/abccacrxqkglrt4qana4/providers/Microsoft.Authorization/roleAssignments/7722b8ef0-9418-4093-z230-152e422cc29d' or the scope is invalid
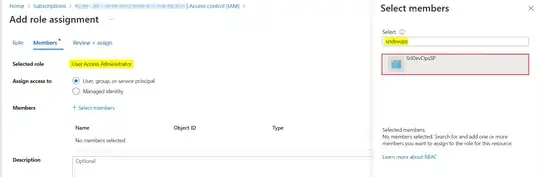
I am able to do the task through my local command line and also i have user access administrator permission on the subscription. The yaml file task is as follows:
- task: AzureCLI@2
inputs:
azureSubscription: $(armDeploymentServiceConnection)
scriptType: 'bash'
scriptLocation: 'inlineScript'
The azureSubscription contains the ARM serviceconnection i created in devops for connecting to ARM
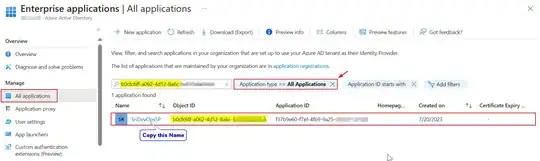
If i search for the client id shown in the devops console error, in the azure portal, it does not exist is the result Can anyone help here? Thanks