To authenticate access to the Azure Function from Azure DPS using a managed identity.
- Enable
Managed Identity for the Azure Function
JWT token for a user in Azure AD

- Grant access to the
Azure Function
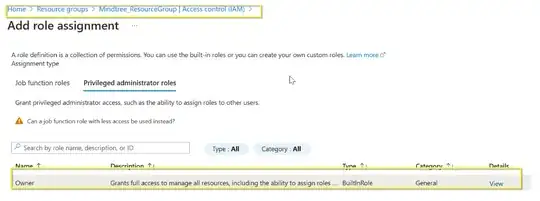
In Azure go to the resource of storage account that the Azure Function needs to access.
Choose Access control (IAM)" settings and add a new role assignment.
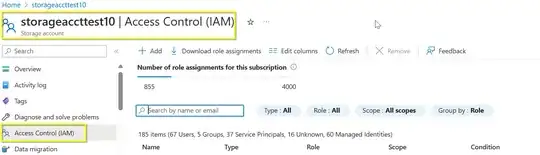
Select the appropriate role based on the required permissions for the Azure Function.
In the "Assign access to" field.
- Modify your Azure Function to validate the managed identity.
In C# code, you can access the identity token from the request headers.
Validate the identity token using the Azure AD token validation endpoint or by using the appropriate library for token validation.
[FunctionName("Function1")]
public static async Task<IActionResult> Run(
[HttpTrigger(AuthorizationLevel.Function, "get", "post", Route = null)] HttpRequest req,
ILogger log)
{
var identity_Token = req.Headers["X-MS-TOKEN-AADIDTOKEN"];
var validation_Params = new TokenValidationParameters
{
ValidateIssuer = true,
ValidIssuer = "https://login.microsoftonline.com/{TenantId}/v2.0",
ValidateAudience = true,
ValidAudience = "Azure fun Client App ID"
};
var tokenHandler = new JwtSecurityTokenHandler();
try
{
var res_principal = tokenHandler.ValidateToken(identity_Token, validation_Params, out _);
return new OkObjectResult(res_principal);
}
catch (Exception ex)
{
log.LogError(ex, "Token validation failed");
return new UnauthorizedResult();
}
}
For more information refer to the MSDoc1 and MSDoc2.





