I have a function app (with python runtime and consumption plan) that once a month must load some data from a public source, process them and put them to an azure blob storage, that instead must remain private.
This flow works when I tested it leaving the blob storage open to public.
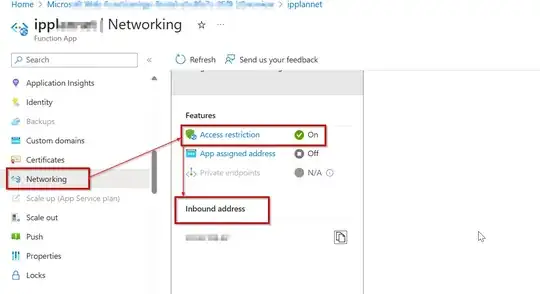
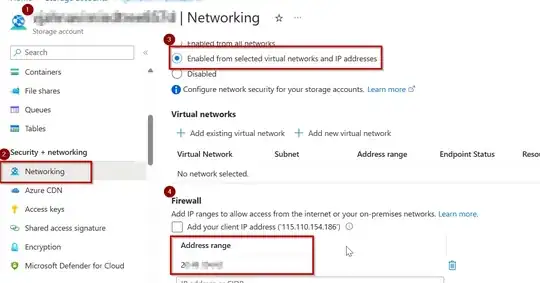
Then I added some ip addresses to the firewall of the blob storage: in particular, my own private ip and all the list of outbound ips available in the "networking" section of the function app. In this case the function cannot communicate with the blob storage and the required files are not written there.
I know there is the possibility to use a premium plan to enable the virtual network integration (that I think it should work smoothly), but I would prefer to not have additional extra costs.
Also, I can use a private endpoint connection, but again this entails to have a premium plan for the app and an higher cost.
Why the function cannot communicate with the storage even if I added all its available outbound ips? Are there any additional ip that is required to be added? I also read this doc, but I cannot find the required information in the JSON file as explained.
Can someone help on this? Many thanks!