BACKGROUND: I have setup a Virtual Network connection in Azure to a local on-premise database. We are connecting an app service (web page) to a local on-premise database, a page is retrieving data from this on-premise database. It kept giving errors every week and the only way to fix it would be restarting the app service, and it would magically work again.
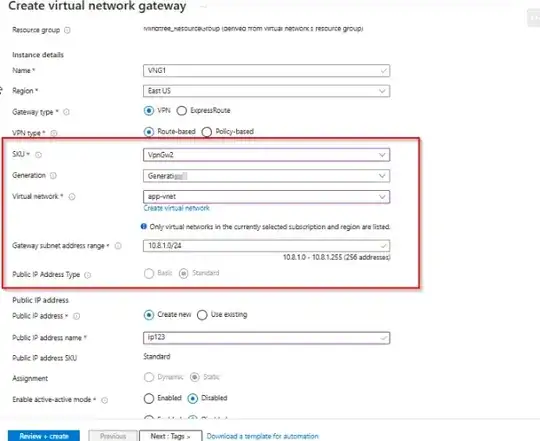
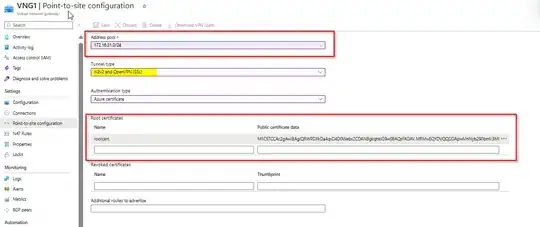
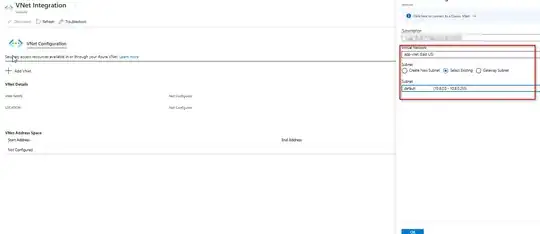
ISSUE: I wanted to try to upgrade the SKU from basic to VpnGw2 to possibly solve the issue where our app service would lose connection to our on-premise database. I set it up the same way I had before but it is asking for a Point-To-Site connection on the VNet Connection (screenshot below)

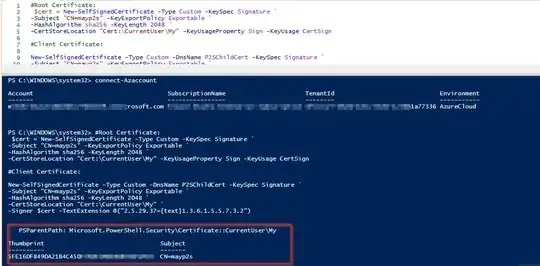
QUESTION: I am not sure how to set up a Point-to-Site configuration with an Azure app service. I am required to enter certificate data, how do I generate a certification on my Azure App Service that can be used for this? Or am I doing something wrong? From what I am reading online, a point-to-site is usually configured for a single machine, I haven't seen anything in regards to an actual app service being configured. Should I use Generate certificates for point-to-site using PowerShell via my Web Service Kudu console?
Some guides I've been using -
Configure server settings for P2S VPN Gateway connections - certificate authentication - Azure portal