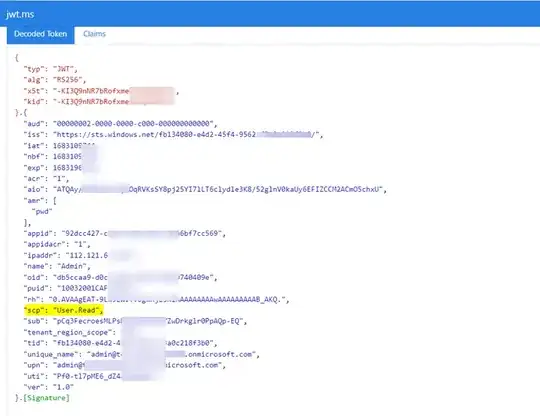
I am currently trying to verify an access token generated using msal python.
I created my ConfidentialClientApplication like this
app = ConfidentialClientApplication(
"<client_id>", #client id
authority="https://login.microsoftonline.com/<tenant_iD>",
client_credential="<client_secret>",
token_cache=cache)
Then i try to create my access token like this
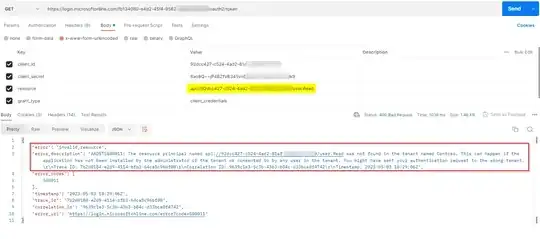
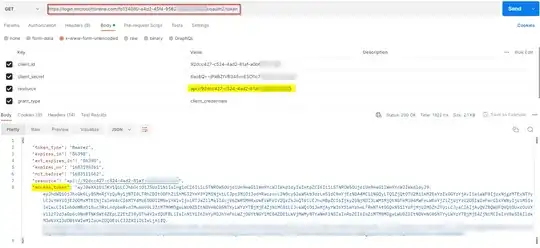
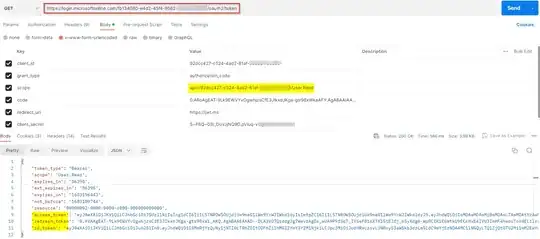
result = app.acquire_token_for_client(scopes=["<scope>/.default"])
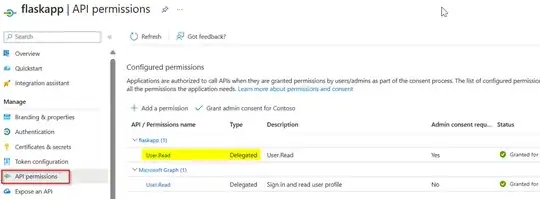
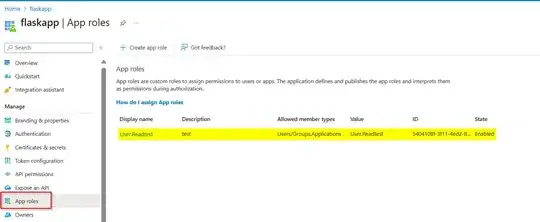
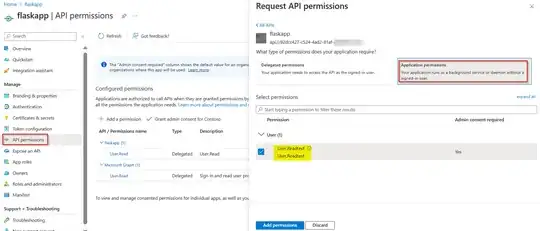
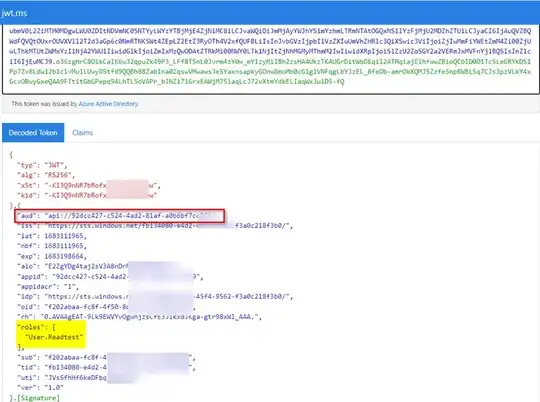
The scope has been exposed on azure portal under "Expose an API" for the resource and has been added by the client under the "API permissions".
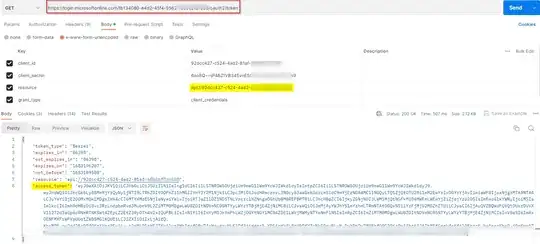
if i do not include the scope name , Tokens are generated just fine.
However, I looked at other examples and i notice some people use their scope together with the scope name
eg : api://<application_uri>/USER.READ as opposed to just the application uri like api://<application_uri>
When i use api://<application_uri>/USER.READ in the scope, i get this error instead
{'error': 'invalid_resource', 'error_description': 'AADSTS500011: The resource principal named api://<application_uri>/USER.READWRITE was not found in the tenant named <tenant name>. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.\r\nTrace ID: 64697571-81b1-4d6c-bd61-fa69c7c97700\r\nCorrelation ID: 3bbc9c0f-39d1-4ca3-b15e-918a10391924\r\nTimestamp: 2023-05-02 07:30:44Z', 'error_codes': [500011], 'timestamp': '2023-05-02 07:30:44Z', 'trace_id': '64697571-81b1-4d6c-bd61-fa69c7c97700', 'correlation_id': '3bbc9c0f-39d1-4ca3-b15e-918a10391924', 'error_uri': 'https://login.microsoftonline.com/error?code=500011'}
cache <msal.token_cache.SerializableTokenCache object at 0x000001946C97FFD0>
I have been trying to look for answers for weeks now, anyone can help?