I'm following this tutorial to authenticate a react application using MSAL and call my own api using the authentication token: https://github.com/oizhaolei/typescript-msal-sample
I added the following code to make an api call:
import { loginRequest, config } from "../authConfig";
import { msalInstance } from "../index";
export async function callMsGraph() {
const account = msalInstance.getActiveAccount();
if (!account) {
throw Error("No active account! Verify a user has been signed in and setActiveAccount has been called.");
}
const response = await msalInstance.acquireTokenSilent({
...loginRequest,
account: account
});
const headers = new Headers();
const bearer = `Bearer ${response.accessToken}`;
headers.append("Authorization", bearer);
const options = {
method: "GET",
headers: headers
};
return fetch(config.endpoint, options)
.then(response => response.json())
.catch(error => console.log(error));
}
authConfig.ts
import { Configuration } from "@azure/msal-browser";
// Config object to be passed to Msal on creation
export const msalConfig: Configuration = {
auth: {
clientId: "<client-id>",
authority: "https://login.microsoftonline.com/<tenant-id>",
redirectUri: "http://localhost:3000/",
postLogoutRedirectUri: "/"
}
};
// scopes
export const loginRequest = {
scopes: ["api://<client-id>/user_impersonation"]
};
// endpoints
export const config = {
endpoint: "https://xxx-webapi.azurewebsites.net/api/v1/jobs"
};
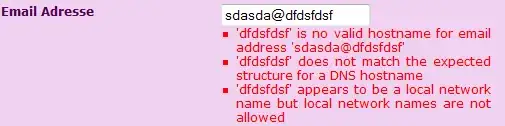
On running this, I see 401 unauthorized error. What am I missing?