I have a vendor application, possibly a SAAS application that want to access my key Vault in my Azure tenant, which is behind a firewall. Can anyone the suggest the best way to give the vendor access to my key vault? please drop a comment if you have done this before.
-
You can use the `managed identity` to grant access to your KV. The external application needs to use this managed identity when trying to read secret values from your KV. see the [documentation](https://learn.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-access-nonaad) for more details. – Anand Sowmithiran Dec 24 '22 at 09:26
1 Answers
There are 2 ways, from which you can give the External vendor application access to your Azure key vault.
You can create a new service principal/app registration in your Azure AD tenant which will model the vendor application and provide that service principal access to key vault secrets and certificates, Via adding that service principal to the access policy with RBAC role. And then giving your vendor the Application client ID, Application secret, Tenant ID to use this app in their SAAS vendor app code for authentication to Key vault in your tenant. If the SAAS Vendor application already resides in your tenant, This method will work too.
I created a key vault resource on Azure :-
I created one single Tenant App to use for this tenant and then added that app to the access policy of Azure key vault.
Select your key vault from Azure Portal> Left pane> Access Policies> Add> Select the secret, key and certificate permissions as required > In Principal select your Single Tenant App> Next> Create
Singletenantapp is added to access policies with below permissions on Key vault:-
Now, You can provide this singletenantkeyvault application’s > tenant Id, application client ID, secret to the SAAS vendor application code as this Singletenantkeyvault application will model your real world SAAS vendor application.
Example-
{
"DNSNameKeyVault": "https://siliconkeyvault123.vault.azure.net/",
"AADAppRegistrationAppId": "7dad56d0-29d7-4d14-8dbe-4b9787895942",
"AADAppRegistrationAppSecret": "<app-secret>",
"SomeSecret": "DEV_VALUE"
}
Similar settings should be added to your SAAS vendor’s application’s appsettings.json folder depending on the framework that the SAAS vendor’s app runs on.
Note- Access policies can only be added to the Users and Applications in your directory only, you cannot add access policies to the external application that resides in other tenant/directory. You can either create a new application in your tenant or enable Multi-tenant application.
- You can create a multi-tenant app shared between your External SAAS vendor’s tenant and your tenant, And assign the Key vault access policy to that Multi-tenant App. In this way you can use the existing SAAS vendor app in their tenant with your tenant to only give least privileged access to control Key vault.
I created a multi-tenant asp.net core app in my Default Directory tenant: -

MultiTenantAuth App is created successfully in our Azure AD Default Directory tenant
You can also create a multi-tenant app within Azure AD portal like below:-
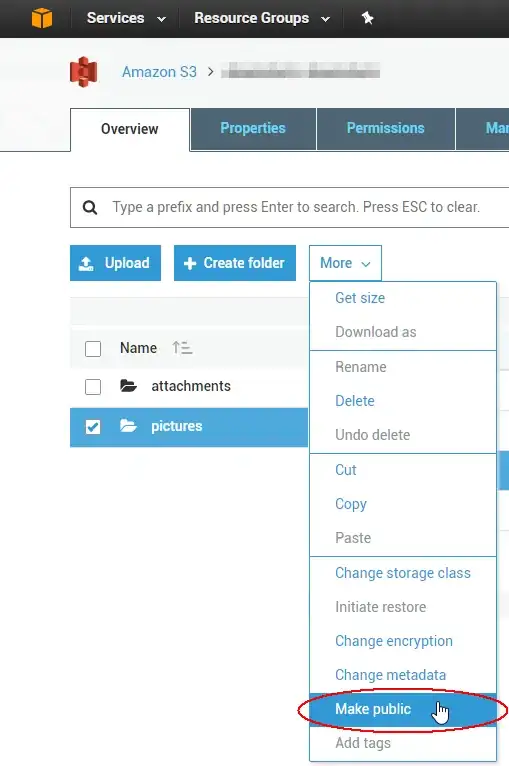
Now, either you can authenticate with your SAS vendor application with your tenant and access key vault via running the code from VS studio or you can call this endpoint and replace the SAS vendor’s tenant ID with yours to get the SAAS vendor application from their tenant to your tenant and then provide the required access:-
In this example- Your MultiTenantDemo or MultiTenantAuth app is your SAAS vendor’s tenant Application which will be added in your or other tenant by either running the code or by calling the below endpoint.
In this example- I created MultiTenantDemo, MultiTenantAuth applications in my Default Directory and now I am adding them in my other directory SiliconSid.
https://login.microsoftonline.com/tenantid/adminconsent?client_id=clientid&state=12345&redirect_uri=http://localhost/myapp/permissions
I logged in with my another tenant’s admin user and accepted the consent for the app from my default directory to the new directory
After I called this endpoint, the Application is added in my another directory SILICONSID:-
Now, I’ll add this application in the Access policy of my key vault :-
- Is inviting the user from your SAAS vendor’s tenant to your tenant and giving the user access to your key vault access policy if your saas vendor real world application uses username and password as authentication and not Service principal.
You can invite your SAAS vendor’s user like below:-
Invite the user and only provide the user access to your key vault:-
You can invite the SAAS vendor user via Email
An invitation link will be sent to the user’s email once the user accepts the invitation, He is redirected to your Azure Portal and is added in your Azure AD.
The SAAS vendor user can log in to Azure Portal and select your directory> and access the Key vault given you added that user to your access policy like below:-

You can again apply the policy of least privileged here and provide user only the access to the key vault and nothing else. You also need to provide the invited user access to your Subscription’s Key vault resource group with key vault role to only read key vault. This can be used if your SAAS vendor real world application uses Username and password as authentication in their Code and not service principal application.
The best way here is to either create a new application in your tenant or to create a multi-tenant application. Point 3) is not recommended and is not a best security practice.
Reference:
Azure Key Vault considerations for multitenancy - Azure Architecture Center | Microsoft Learn
- 814
- 1
- 9
-
Thank you for the answer and I really appreciate the detailed answer. First of all, this ia a Production environment and we have the first option in place, we can see that the vendor App can authenticate to Key Vault, because we already set up access policy for service principal/App registration of the Vendor App, but they can get access Key Vault. My question is, in the Enterprise Application do we have to give them a role and what kind of role? – barry Dec 29 '22 at 21:26