Replicated the requested change via terraform. Here is a code snippet for adding the KPL query using the Terraform implementation.
**NOTE: The query snippet mentioned is invalid; we can review it on the Azure portal before applying.
Got to Application Insights -> Logs [Monitor] -> Click on any query and validate before implement. **
Step1:
Insert the following code into the main tf file. added a sample query for testing via Terraform.
provider "azurerm" {
features {}
}
resource "azurerm_resource_group" "example" {
name = "Resource-Group-Dev"
location = "West Europe"
}
resource "azurerm_application_insights" "example" {
name = "appinsights"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
application_type = "web"
}
resource "azurerm_monitor_scheduled_query_rules_alert" "example" {
name = "examplealert"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
action {
action_group = []
email_subject = "Email Header"
custom_webhook_payload = "{}"
}
data_source_id = azurerm_application_insights.example.id
description = "Alert when total results cross threshold"
enabled = true
query = format(<<-QUERY
let a=requests
| where toint(resultCode) >= 500
| extend fail=1; let b=app('%s').requests
| where toint(resultCode) >= 500 | extend fail=1; a
| join b on fail
QUERY
, azurerm_application_insights.example.id)
severity = 1
frequency = 5
time_window = 30
trigger {
operator = "GreaterThan"
threshold = 3
}
}
variable "prefix" {
default = "tfvmex"
}
resource "azurerm_virtual_network" "main" {
name = "${var.prefix}-network"
address_space = ["10.2.0.0/16"]
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
}
resource "azurerm_subnet" "internal" {
name = "internal"
resource_group_name = azurerm_resource_group.example.name
virtual_network_name = azurerm_virtual_network.main.name
address_prefixes = ["10.2.2.0/24"]
}
resource "azurerm_network_interface" "main" {
name = "${var.prefix}-nic"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
ip_configuration {
name = "testconfiguration1"
subnet_id = azurerm_subnet.internal.id
private_ip_address_allocation = "Dynamic"
}
}
resource "azurerm_virtual_machine" "main" {
name = "VM-Dev-1"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
network_interface_ids = [azurerm_network_interface.main.id]
vm_size = "Standard_DS1_v2"
storage_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "16.04-LTS"
version = "latest"
}
storage_os_disk {
name = "myosdisk1"
caching = "ReadWrite"
create_option = "FromImage"
managed_disk_type = "Standard_LRS"
}
os_profile {
computer_name = "hostname"
admin_username = "testadmin"
admin_password = "Password1234!"
}
os_profile_linux_config {
disable_password_authentication = false
}
tags = {
environment = "dev1"
}
}
//VM2
resource "azurerm_virtual_network" "main2" {
name = "${var.prefix}-network2"
address_space = ["10.1.0.0/16"]
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
}
resource "azurerm_subnet" "internal2" {
name = "internal"
resource_group_name = azurerm_resource_group.example.name
virtual_network_name = azurerm_virtual_network.main2.name
address_prefixes = ["10.1.2.0/24"]
}
resource "azurerm_network_interface" "main2" {
name = "${var.prefix}-nic2"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
ip_configuration {
name = "testconfiguration2"
subnet_id = azurerm_subnet.internal2.id
private_ip_address_allocation = "Dynamic"
}
}
resource "azurerm_virtual_machine" "main2" {
name = "VM-Dev-2"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
network_interface_ids = [azurerm_network_interface.main2.id]
vm_size = "Standard_DS1_v2"
storage_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "16.04-LTS"
version = "latest"
}
storage_os_disk {
name = "myosdisk2"
caching = "ReadWrite"
create_option = "FromImage"
managed_disk_type = "Standard_LRS"
}
os_profile {
computer_name = "hostname1"
admin_username = "testadmin2"
admin_password = "Password123!"
}
os_profile_linux_config {
disable_password_authentication = false
}
tags = {
environment = "dev2"
}
}
Step2:
Execute below commands
terraform plan

terraform apply -auto-approve
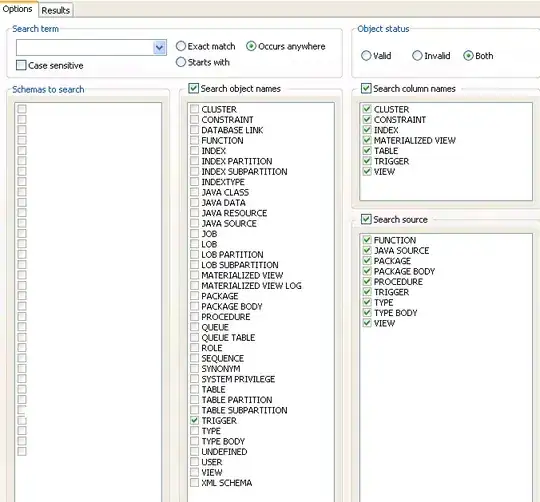
Verification from the portal

Hope this helps!





