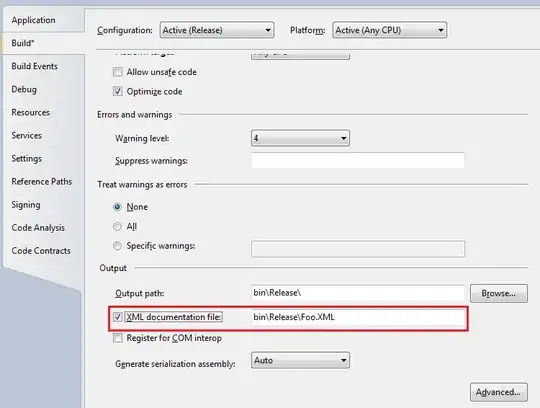
This is the architecture I want to follow
Source: What exactly is redirect_uri in Google OAuth2 request for getting authorization code in Mobile App?
I'm using a backend to exchange tokens with the authorization code, then send the tokens back to the frontend via set-cookie header.
Would PKCE be required for this case? I think it's unnecessary here since the client secrets can be safe in the Django server, just wanted a confirmation as I'm new to this realm.
Also, I'll be encrypting the state parameter in the front-end, and decrypting it in the backend probably using asymmetric keys.
Is there any security vulnerability in all of these approaches?
EDIT:
If PKCE is required, how could we share the code verifier between the client and the server?