I tried to reproduce the same in my environment and got below results
I registered one Azure AD application and granted API permissions as below:
Now I generated access token via Postman with below parameters:
POST https://login.microsoftonline.com/<tenantID>/oauth2/v2.0/token
client_id:appID
grant_type:client_credentials
client_secret:secret
scope:05a65629-4c1b-48c1-a78b-804c4abdd4af/.default
Response:

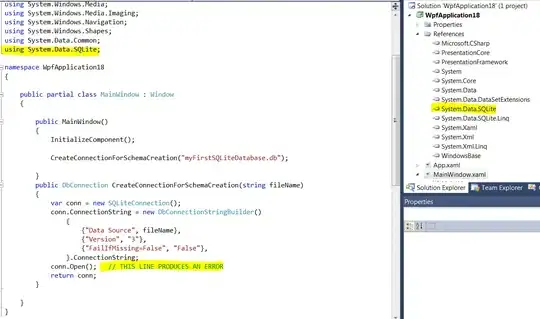
When I used the above token to get files with both URLs, I got same error as below:
GET https://portal.cloudappsecurity.com/cas/api/v1/files/
Authorization: Bearer <token>
GET https://mytenantname.us3.portal.cloudappsecurity.com/api/v1/files/
Authorization: Bearer <token>
With the same token, I'm able to call all other APIs like alerts, activities etc. like below:
GET https://mytenantname.us3.portal.cloudappsecurity.com/api/v1/alerts/
Authorization: Bearer <token>
Note that, calling file APIs is not available in application
context.
Alternatively, you can make use of Legacy Method by generating one API token like below:
Go to Defender for Cloud Apps portal -> Settings -> Security extensions -> API tokens -> Add a token
Now, enter Token name and select Generate as below:
API token will be generated successfully and copy the token to use in Postman:
When I used the above API token to call files API with both URLs, I got response successfully as below:
GET https://portal.cloudappsecurity.com/cas/api/v1/files/
Authorization: Token <token>
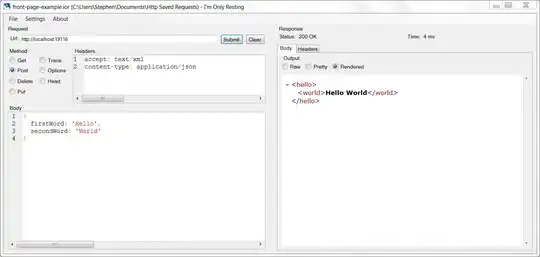
GET https://mytenantname.us3.portal.cloudappsecurity.com/api/v1/files/
Authorization: Token <token>
You can try the same in your environment by generating API token instead of Bearer token to call Files API.
Reference:
Defender for Cloud Apps file API “Insufficient role based permissions” by Sangho Cho