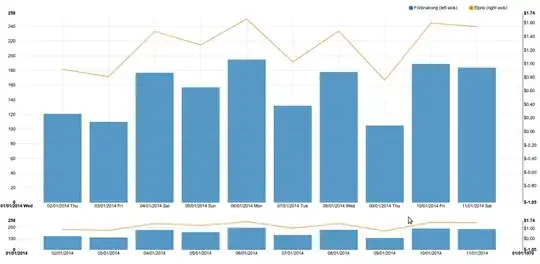
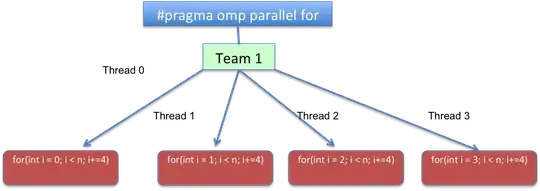
I followed https://www.youtube.com/watch?v=TRrBqNYtyj8 video to secure my backend API using Azure API management. After following the steps the workflow was not working and I had to add an additional step. After adding the step, I got oAuth workflow working.
But I wonder if this is the right way to implement oAuth workflow? As per this article, I am suppose to add inbound policy which I have not implemented. Please provide suggestions
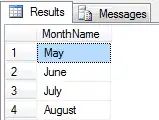
I followed following steps:
Using Azure AD add backend application.
Go to Manifest and update
accessTokenAcceptedVersionto 2 and save. Set theappId URIfor backend app &add scopeEnable authentication for backend API. In the
Redirect URI'stextbox, after backend api url add/.auth/login/aad/callbackNow go to back to
app service(assuming App service is hosting your backend api) >Authentication > Add an identity provider> from next window selectMicrosoft as identity providerand select Pick anexisting app registrationin this directory radio button from app registration type. Keep remaining settings as default and click add.At this point of time your backend api is secure.
Register client app
Grant Permission. After granting permission, Click on Manifest and change value of
accessTokenAcceptedVersionto2Now select
api permission> Click +add permission> selectMy API’stab > select the backend app we created and select scope & clickAdd permissions.Create Client Certificate: Under client app, select
Certificates & Secrets> Click on +New Client Secret> provide a some description & click Add.
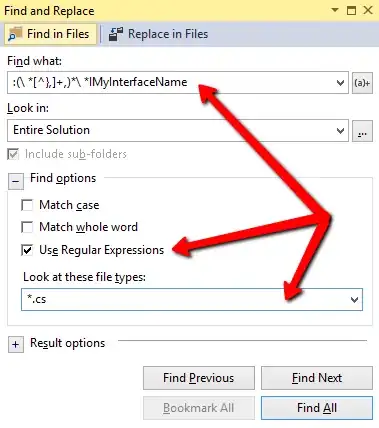
Following are additional steps I added which was not available in video: