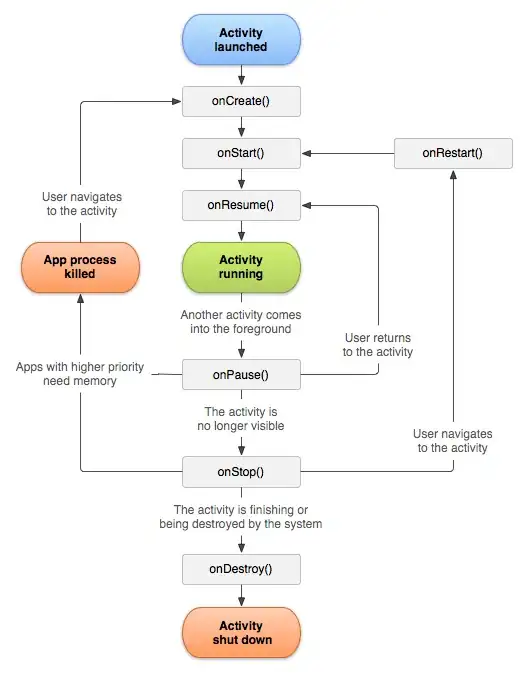
I do not think this is possible through a Resource Graph Query. One possible approach would be to use Azure REST API subsequently to get the results. Here is a PowerShell example:
You need to generate a Bearer token in order to query the REST API. You could use a function like this to generate it.
function Get-AzOauth2Token
{
[CmdletBinding()]
Param
(
[string]$TenantId,
[string]$AppId,
[string]$Secret
)
$result = Invoke-RestMethod -Uri $('https://login.microsoftonline.com/'+$TenantId+'/oauth2/token?api-version=1.0') -Method Post -Body @{"grant_type" = "client_credentials"; "resource" = "https://management.core.windows.net/"; "client_id" = "$AppId"; "client_secret" = "$Secret" }
$authorization = ("{0} {1}" -f $result.token_type, $result.access_token)
return $authorization
}
There are a lot of other ways to get a token though. However, I will use this to retrieve it...
$token = Get-AzOauth2Token -TenantId your_tenant -AppId your_spn_app_id -Secret your_secret
Then you would run your resource graph query in order to get all Function Apps across the tenant and in any subscription.
$query = Search-AzGraph "resources | where type =~ 'microsoft.web/sites' | where kind startswith 'functionapp'"
$results = Search-AzGraph -Query $query
...and finally execute the REST API Calls for all the Function Apps that the query returned.
$functions = @()
$results | ForEach-Object {
$restMethod = 'GET'
$restUri = 'https://management.azure.com'+$_.ResourceId+'/functions?api-version=2022-03-01'
$restHeader = @{
'Authorization' = $token
'Content-Type' = 'application/json'
}
# Execute Call
$request = Invoke-RestMethod -Method $restMethod `
-Uri $restUri `
-Headers $restHeader
$functions += $request
}
The $functions.value variable now holds all the different functions.
I suggest using the REST API instead of standard PowerShell cmdlets because it is faster in large environments - it prevents you from having to switch between subscriptions when you have resources spread across various subscriptions.