My question then is, is there a way to manually decrypt the column encryption key using a valid RSA key?
Yes, you can manually decrypt the column encryption key and master key using Always Encrypted with secure enclaves, but these features are only allowed in DC-series hardware configuration along with Microsoft Azure Attestation which are available only in few Locations. So, you need to select a location (an Azure region) that supports both the DC-series hardware and Microsoft Azure Attestation.
Note: DC-series is available in the following regions: Canada Central, Canada East, East US, North Europe, UK South, West Europe, West US.
Choose DC-series while deploying the SQL Database by following the steps below.
Make sure to SQL Server is deployed in DC-series supported location. Click on configure database.
Select hardware configuration
Select DC-series, click on OK, Apply and deploy the database.

Now create attestation provider using Azure Portal. Search for attestation in search bar and select Microsoft Azure Attestation.
On the Overview tab for the attestation provider, copy the value of the Attest URI property to clipboard and save it in a file. This is the attestation URL, you will need in later steps.

Select Policy on the resource menu on the left side of the window or on the lower pane.
Set Attestation Type to SGX-IntelSDK.
Select Configure on the upper menu.
- Set Policy Format to Text. Leave Policy options set to Enter policy.
- In the Policy text field, replace the default policy with the below policy.
[ type=="x-ms-sgx-is-debuggable", value==false ]
&& [ type=="x-ms-sgx-product-id", value==4639 ]
&& [ type=="x-ms-sgx-svn", value>= 0 ]
&& [ type=="x-ms-sgx-mrsigner", value=="e31c9e505f37a58de09335075fc8591254313eb20bb1a27e5443cc450b6e33e5"]
=> permit(); }; ```
Configure your database in SSMS. Click on Options and give attestation URL which you have copied in step 5.
Using the SSMS instance from the previous step, in Object Explorer, expand your database and navigate to Security > Always Encrypted Keys.
Provision a new enclave-enabled column master key:
Right-click Always Encrypted Keys and select New Column Master Key....
Select your column master key name: CMK1.Make sure you select either Windows Certificate Store (Current User or Local Machine) or Azure Key Vault.
Select Allow enclave computations.

- Now simply encrypt your column. See below example to encrypt.
ALTER TABLE [HR].[Employees]
ALTER COLUMN [SSN] [char] (11) COLLATE Latin1_General_BIN2
ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL
WITH
(ONLINE = ON);
ALTER TABLE [HR].[Employees]
ALTER COLUMN [Salary] [money]
ENCRYPTED WITH (COLUMN_ENCRYPTION_KEY = [CEK1], ENCRYPTION_TYPE = Randomized, ALGORITHM = 'AEAD_AES_256_CBC_HMAC_SHA_256') NOT NULL
WITH
(ONLINE = ON);
ALTER DATABASE SCOPED CONFIGURATION CLEAR PROCEDURE_CACHE;
Verify the encrypted data.
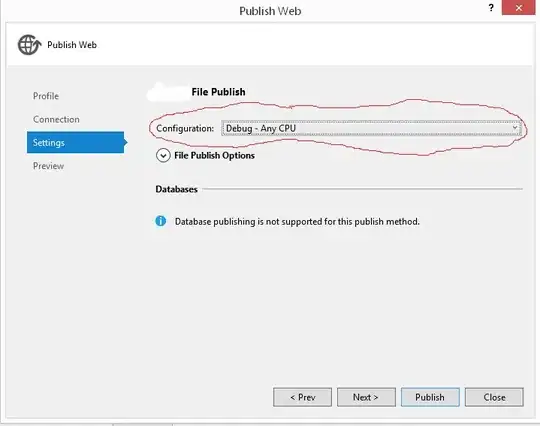
- To decrypt using customer encrypt key, see below example.
ALTER TABLE [HR].[Employees]
ALTER COLUMN [SSN] [char](11) COLLATE Latin1_General_BIN2
WITH (ONLINE = ON);
GO










