We are setting up an Azure App Service (Web app) that needs to get some secrets from a Key vault. For this, we have enabled System assigned identity for the web app. The Key vault is using RBAC and we decided to create an Azure AD group to give access. We added a role assignment (Key Vault Secrets Officer) on the Key vault for the Azure AD group.
In the app service, I can go to "Identity" and press on the button for "Azure role assignments". Here I see the role assignment made:
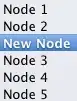
However, if I go to Application settings, it says that it does not have access. I have given it about 3 hours, without success. I have restarted and updated other settings to trigger restart.
If I put myself to this Azure AD group I get access to go and work with secrets.. Any ideas why this is the case? Is this not supported for RBAC yet?
Thanks!