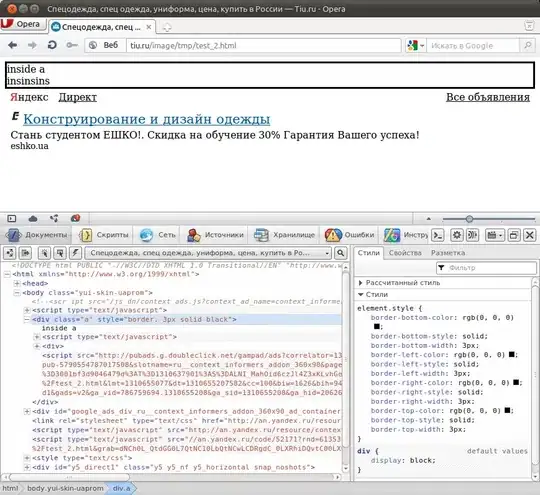
I'm using Jelastic with two environments, one for my frontend and one for my backend.
Each environment has a Nginx load balancer with an IPv4, then an application server. For the backend (api), the application server is Spring-boot and for the frontend, it is Node.js
However, I have added IPv4 on each of my application servers to have direct access with my deployment scripts.
The concern now is that if I go directly through these IPs and no longer through the respective load balancers, I can still access my application but the connection is not secure.
I tried to close the incoming ports 80/443 on the application servers, but it doesn't change anything, I still access with the IP.
Here is an image that quickly summarizes the problem (the ip used are not real):
Thank you for your help
EDIT :