In the root account, I have a verified domain identity that I used to create an email identity for transactional emails.
Now, I created a new IAM account.
I would like to attach a policy to this IAM account that allows it to create a verified email identity using that verified domain identity in the root account.
And he must not be able to list nor use the verified email identity in the root account.
Should I use an inline policy for this (which I know should be avoided and left as a last resort) or normal permission configuration?

If so how should I write or pick such a policy?
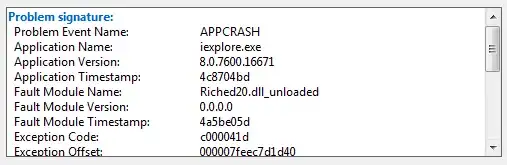
EDIT 1: When I tried to create an email using the IAM account, just to see what AWS would say, this is what's written in the notification:
You do not have sufficient access to perform this action.
User: arn:aws:iam::122443365328:user/iam-user-name is not authorized to perform: ses:CreateEmailIdentity on resource:
arn:aws:ses:us-region:122443365328:identity/test@dmain_name.com because no identity-based policy allows the ses:CreateEmailIdentity action
And when I searched for the CreateEmailIdentity in the inline policy creation dashboard, it was not found:
EDIT 2:
I have actually found it when I picked SES-v2 as a service:
I have granted the IAM user these privileges:
I added the ARN of the verified domain name:
This is the result:
But, still when I try to create an email identity using the IAM account, I still get this:
You do not have sufficient access to perform this action. User: arn:aws:iam::12xxxxxx5328:user/iam-user-name is not authorized to perform: ses:CreateEmailIdentity on resource: arn:aws:ses:us-west-2:122443365328:identity/dev@domain_name.com because no identity-based policy allows the ses:CreateEmailIdentity action
What I don't understand here is the meaning of not being authorized to perform ses:CreateEmailIdentity on the resource that I am trying to create which is the new email.
How can I be authorized to do that on an email identity that still doesn't exist.
EDIT 3:
Even after created an email using the root user and granted the IAM user the privilege of sending emails using that email using this policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "stmt1643366831422",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::12xxxxxx328:user/iam-user-name"
},
"Action": [
"ses:SendEmail",
"ses:SendRawEmail",
"ses:SendTemplatedEmail",
"ses:SendBulkTemplatedEmail"
],
"Resource": "arn:aws:ses:us-west-2:12xxxxxxxx28:identity/test2@domain_name.com",
"Condition": {}
}
]
}
When I send email in the backend, this is what gets logged:
~ file: emailServices.js ~ line 297 ~ .then ~ error AccessDenied: User
arn:aws:iam::12xxxxx5328:user/iam-user-name' is not authorized to performses:SendEmail' on resource `arn:aws:ses:us-west-2:1xxxxx28:identity/domain_name.com'
Then I authorized the iam user to send email on the Domain Identity using the same policy but applied on the Domain Identity.
Now, sending emails using the IAM user credentials works.
The problem is that he can send emails using all verified email idenitities.
But, I want him to be able to do so by only using the corresponding email identity that was created specifically for that IAM user.
NOTE 1:
I am aware that I should not use the root account and should instead only use IAM accounts.