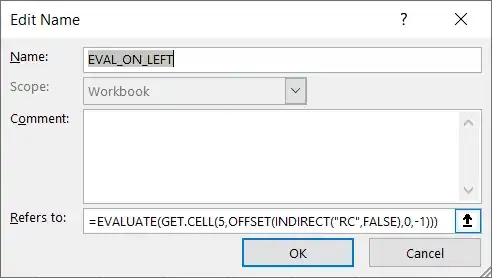
I am having the below piece of ASP.NET code to load a pfx file from a folder
var certificatePath = $"{HttpContext.Current.Server.MapPath("~")}{certFolderName}\\{certFileName}";
return new X509Certificate2(certificatePath, certPassword, X509KeyStorageFlags.MachineKeySet);
This code works fine in local IIS. However the same code when moved to our QA servers its throws Access Denied error as below.
I had gone through many forums and got to know that this is mostly a permission issue in accessing the folder C:\ProgramData\Microsoft\Crypto\RSA\MachineKey. I have verified the access for this folder in our server and its all fine. The 'Everyone' user has read & write access. So ideally there shouldn't be any access denied error. I even gave explicit Full Control access to the identity of App Pool, but still doesn't work. I am trying to understand what else could cause this access denied problem.