I am trying to secure client daemon communication on windows by creating a certificate authority (CA).
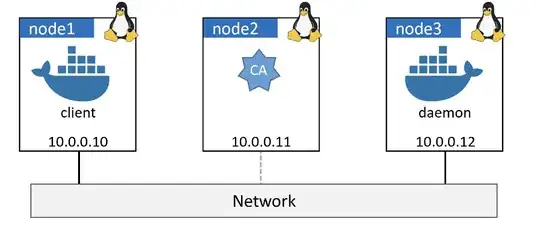
The lab setup shown in the above image is used in the example but it says my lab will be different but I don't know how to find the IP addresses like 10.0.0.10, 10.0.0.11 and 10.0.0.12. I know the node names are docker.exe (client) and dockerd.exe (daemon) but what are their IP addresses?
The default installation puts them on the same host and configures them to communicate over a local IPC socket: //./pipe/docker_engine
It's also possible to configure them to communicate over the network. By default, network communication occurs over an unsecured HTTP socket on port 2375/tcp
I don't know what information in this is relevant or helpful but I need to know the IP addresses of the docker daemon and client.
In answer to the responses I am also writing this: I am following along with the book Docker Deep Dive and I am trying to secure client daemon communication. I am creating a file called extfile.cnf which has the following inside: subjectAltName = DNS:node3,IP=10.0.0.12 extendedKeyUsage = serverAuth
I need to know what to put instead of 10.0.0.12
When I put localhost/127.0.0.1/127.0.0.1:2375/tcp://127.0.0.1:2375 or anything else and then run the command afterwards which is this:
openssl x509 -req -days 730 -sha256 -in daemon.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out daemon-cert.pem -extfile extfile.cnf
The error is:
x509: Error on line 1 of config file "extfile.cnf" 7C0A0000:error:07000065:configuration file routines:def_load_bio:missing equal sign:crypto\conf\conf_def.c:511:HERE--> ■sline 1