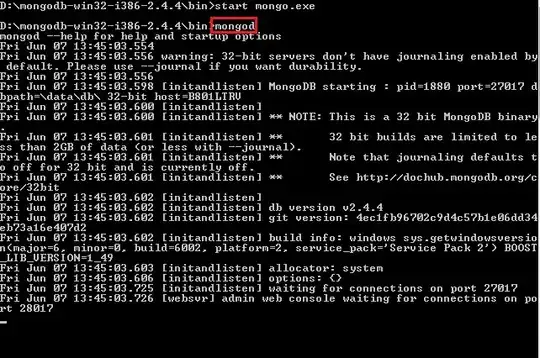
When attempting a web request to a site which requires TLS 1.3 https://shop.claytonengineering.com/. I'm receiving the following exception on "request.GetResponse();".
Exception: The SSL connection could not be established, see inner exception. Inner Exception: The client and server cannot communicate, because they do not possess a common algorithm.
From Google Chrome Developer tools Security tab - "The connection to this site is encrypted and authenticated using TLS 1.3, X25519, and AES_128_GCM."
Any ideas on how to get this request to work?
HttpWebResponse response = null;
HttpWebRequest request = (HttpWebRequest)WebRequest.Create("https://shop.claytonengineering.com/");
request.KeepAlive = true;
request.Headers.Add("Upgrade-Insecure-Requests", @"1");
request.UserAgent = "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36";
request.Headers.Add("Sec-Fetch-Mode", @"navigate");
request.Headers.Add("Sec-Fetch-User", @"?1");
request.Accept = "text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3";
request.Headers.Add("Sec-Fetch-Site", @"same-origin");
request.Headers.Set(HttpRequestHeader.AcceptEncoding, "gzip, deflate, br");
request.Headers.Set(HttpRequestHeader.AcceptLanguage, "en-US,en;q=0.9");
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls13;
response = (HttpWebResponse)request.GetResponse();
string html = null;
using (StreamReader stream = new StreamReader(response.GetResponseStream(), Encoding.UTF8))
{
html = stream.ReadToEnd();
}