I try to build an ARM Template to create Automation Account with System Managed Identity, and in the same template add role assignment on the Subscription level to that System Managed Identity. The code I use is:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"AutomationAccountName": {
"type": "string",
"metadata": {
"description": "Automation account name"
}
},
"AutomationAccountProductTag": {
"type": "string",
"metadata": {
"description": "Automation account Product tag"
}
},
"AutomationAccountOwnerTag": {
"type": "string",
"metadata": {
"description": "Automation account Owner tag"
}
},
"WindowsRunbookName": {
"type": "string",
"metadata": {
"description": "Runbook name for Windows instances"
}
},
"RolesToAssignForMangedIdentity": {
"type": "array",
"defaultValue": [
{
"name": "StorageQueueDataContributor",
"role": "[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Authorization/roleDefinitions/', '974c5e8b-45b9-4653-ba55-5f855dd0fb88')]"
},
{
"name": "Contributor",
"role": "[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Authorization/roleDefinitions/', 'b24988ac-6180-42a0-ab88-20f7382dd24c')]"
},
{
"name": "StorageBlobDataContributor",
"role": "[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Authorization/roleDefinitions/', 'ba92f5b4-2d11-453d-a403-e96b0029c9fe')]"
},
{
"name": "VirtualMachineContributor",
"role": "[concat('/subscriptions/', subscription().subscriptionId, '/providers/Microsoft.Authorization/roleDefinitions/', '9980e02c-c2be-4d73-94e8-173b1dc7cf3c')]"
}
]
}
},
"variables": {
"WindowsRunbookURL": "https://infraawsssmagentinstall.blob.core.windows.net/awsssmagentfiles/Runbook_install_ssm_windows.ps1",
"LinuxRunbookURL": "",
"RunbookRuntime": "5.1"
},
"resources": [
// create automation account //
{
"type": "Microsoft.Automation/automationAccounts",
"apiVersion": "2021-06-22",
"name": "[parameters('AutomationAccountName')]",
"location": "[resourceGroup().location]",
"tags": {
"Product": "[parameters('AutomationAccountProductTag')]",
"Owner": "[parameters('AutomationAccountOwnerTag')]"
},
"identity": {
"type": "SystemAssigned"
},
"properties": {
"sku": {
"name": "Basic"
}
}
},
{
"type": "Microsoft.Resources/deployments",
"apiVersion": "2021-04-01",
"name": "[concat(parameters('RolesToAssignForMangedIdentity')[copyIndex()].name, '_' , guid(parameters('RolesToAssignForMangedIdentity')[copyIndex()].name)) ]",
"copy": {
"name": "RolesCopy",
"count": "[length(parameters('RolesToAssignForMangedIdentity'))]"
},
"properties": {
"mode": "Incremental",
"expressionEvaluationOptions": {
"scope": "outer"
},
"template": {
"$schema": "https://schema.management.azure.com/schemas/2018-05-01/subscriptionDeploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"resources": [
{
"type": "Microsoft.Automation/automationAccounts/providers/roleAssignments",
"apiVersion": "2021-04-01-preview",
"name": "[concat( parameters('AutomationAccountName'), '/Microsoft.Authorization/', guid(parameters('RolesToAssignForMangedIdentity')[copyIndex()].name))]",
"properties": {
"roleDefinitionId": "[parameters('RolesToAssignForMangedIdentity')[copyIndex()].role]",
"principalId": "[reference(resourceId('Microsoft.Automation/automationAccounts', parameters('AutomationAccountName')), '2021-06-22', 'full').identity.principalId]",
"principalType": "ServicePrincipal"
}
}
]
}
}
}
// assigne roles to created managed identity from automation account
],
"outputs": {}
}
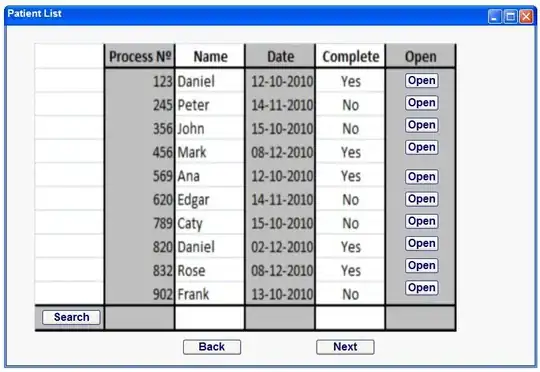
It is adding the role but only for that Automation Account like in picture below:
And what I need is: