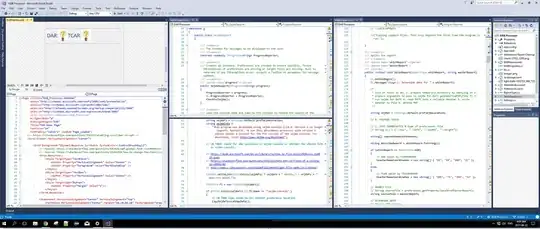
I have two GCP projects. projectA contains an artifact registry where I store my docker images, projectB is where I want to use such an image to deploy it with app-engine (flexible).
Here's how my command looks like:
gcloud app deploy --project=projectB --version=test1 --image-url="asia-northeast1-docker.pkg.dev/projectA/default/my-image:latest"
It fails like this:
ERROR: (gcloud.app.deploy) Error Response: [7] The App Engine appspot and App Engine flexible environment service accounts must have permissions on the image [asia-northeast1-docker.pkg.dev/projectA/default/my-image:latest]. Please check that the App Engine default service account has the [Storage Object Viewer] role and the App Engine Flexible service account has the App Engine Flexible Environment Service Agent role
I ensured that the App Engine default service account has the Storage Object Viewer role (in both projects), however I cannot find an App Engine Flexible service account anywhere.