I'm a bit confused, I have the following implementation:
ASP.net API protected using Azure AD, and users with Admin role only can call this API, these roles are configured in Azure AD and assigned to users. the API has one defined scope AccessApi.
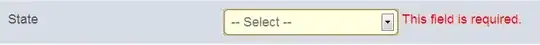
Scopes Who can consent Admin consent display name User consent display name State
api://xx User AccessApi AccessApi Enable
The client application developed in WebAssembly blazor is registered and protected in Azure AD without roles, its configured to use AccessApi scope from my Api.
API / Permissions name Type Description Admin consent required Status
myApi (1)
AccessApi Delegated AccessApi No
My confusion is do I need to assign an Admin role for the client application to obtain token which will be used to access the API or the API scope accessApi is enough without any roles?
knowing that users of the client app are the same users of the API just with different roles.
Since same users use both API and client App, is it possible to use MS Graph by client App to get JWT token and use that token to call the API?