I have a bucket called "payroll-manager". I am able to put objects, etc using cognito authenticated users, I modified the role of my identity pool to have full access to s3 (I followed this example). So far so good.
Now I need to change my policy to allow users to only read, write, etc from their own folder. I google on how to do it and I found this example from AWS. I removed the full access to s3 policy from my cognito role and created a policy following this example, the problem is that I always get a forbidden message.
I opened the IAM policy simulator and I find out that I can not even set this simple policy because it always denies me the permission:
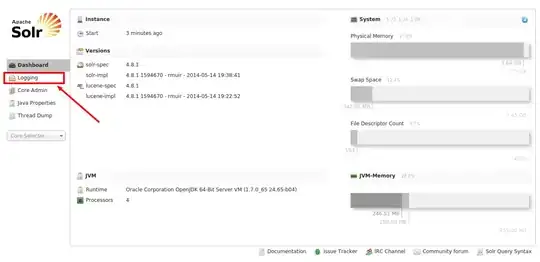
If I change the resource to "*" it allows me:
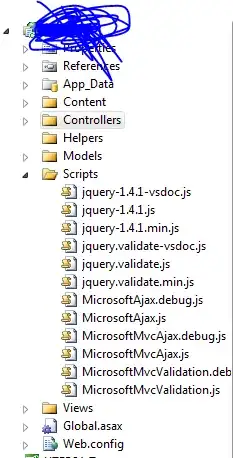
In this example (I only have 1 bucket). Shouldn't be the same to use the resource with * or with ARN?