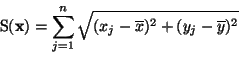I have a valid unexpired code signing certificate (standard, not EV) that I have used to sign a click once app (.net 4.5) successfully and publish to a web server for download. When downloading this app, it shows the publisher name correctly. The problem is, after installing the code signing certificate on any other app, it shows the publisher name as "Unknown publisher" when downloading. There isn't any difference in how I'm installing the certificate and all apps get published to the same web server. When I open the .exe or manifest file when logged into the web server, it shows the publisher name correctly. Checking the "Digital Signatures" file properties shows that they are signed with the correct code signing certificate with sha256. Below are the steps I have used:
- Installed code signing certificate to click once app via the Signing tab and it is enabled (Visual Studio 2017 Pro).
- Code signing algorithm is sha256RSA with valid timestamp server (http://timestamp.comodoca.com/?td=sha256).
- Click once app assembly is not signed.
- Code signing certificate has been installed on dev machine (Windows 10 Pro 1809).
- Code signing certificate has been installed on web server in "Trusted Root Certification Authorities" and "Intermediate Certification Authorities" (Windows 2012 R2 using IIS 8) for the "Computer account".
On a side note, I exported the code signing certificate from Internet Explorer with SHA1 and installed it to the web server afterwards. There is a known issue that when the certificate has been exported to SHA256 and trying to import it to the web server, that the password for the file will always say incorrect. This happened to me, so I just imported the SHA1 version to the web server. Not sure if that would create any issues, but it is working for the one clickonce app ok.
Update: I noticed something peculiar if I go to the publish deployment URL and click the "Install" button. After the setup.exe has been downloaded for the clickonce apps with "Unknown publishers", I am presented with a more dire smart screen filter saying the file is not signed, but shows the correct publisher information below it. Checking the "digital signatures" property for the exe shows that it is signed properly.