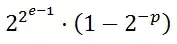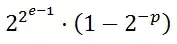I can reproduce your issue, the command Remove-AzRoleAssignment will call the Azure AD Graph to validate the $objectid you passed, so you need give the Application permission Directory.Read.All of Azure AD Graph(not Microsoft Graph,not Delegated permission).
After adding the permission, there is some delay(30m - 1h), then test the command, it works. (I test in local, the same in cloud shell)
Note: Except the permission in Azure AD, your service principal also need to have the permission in the subscription/specific resource scope, e.g. the servcie principal is the Owner/User Access Admin role in the Access control (IAM) of the subscription/specific resource scope(in your case, the storage account). If the service principal does not have the role, please add it as below.
In Azure Devops, you don't need to login with Connect-AzAccount(Actually in cloud shell, you also don’t need to login, but if you want to do so, it's also ok), it will login automatically with the service principal related to the service connection(Task version >= 4.*).
So please make sure the secret of your service principal is correct and the connection was verified. To run Remove-AzRoleAssignment, also add the permission above for the App Registration related to the service connection.
Then test it, it works.