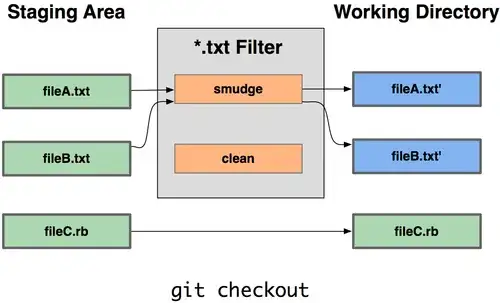
When using Azure Managed Identity in the App Service/Functions, the endpoint and header are available as environment variables.
When using Azure Managed Identity in Virtual Machine, the endpoint is published as the Azure Instance Metadata service (IMDS) (http://169.254.169.254/metadata/identity/oauth2/token), accessible only from within the VM.
On a VM, is the endpoint set as an environment variable (MSI_ENDPOINT)?
On a VM, is there an indication whether managed identity is enabled?
Ideally, my code can simply check for that variable. Otherwise, I need to check the variable and make a call to the IMDS.