I want to access Microsoft Graph periodically from a console application in order to copy messages from an Outlook mailbox to a database. In order to authenticate programmatically, I had to use the Microsoft Graph's "Client Credentials Flow".
These are the steps I had to take:
- Register an App in the Azure portal and create a Client Secret for it.
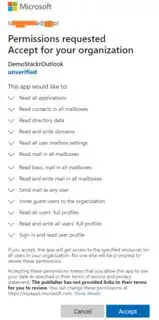
Add all the permissions I need and grant them access:
Have an Admin confirm those permissions by accessing it for the first time. This is done using the following URL:
https://login.microsoftonline.com/{tenant}/v2.0/adminconsent ?client_id={app id} &state=1234 &redirect_uri=https://login.microsoftonline.com/common/oauth2/nativeclient &scope=https://graph.microsoft.com/.defaultI received the following response:
admin_consent: True tenant: ca566779-1e7b-48e8-b52b-68********** state: 12345 scope**: scope: https://graph.microsoft.com/User.Read https://graph.microsoft.com/.default(The scope might explain the problem described later here: Why do I only get
User.Readwhen I've configured 13 different permissions??)Get an access token (with success!):
Try to read users (with success):
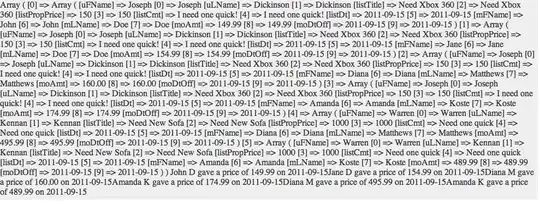
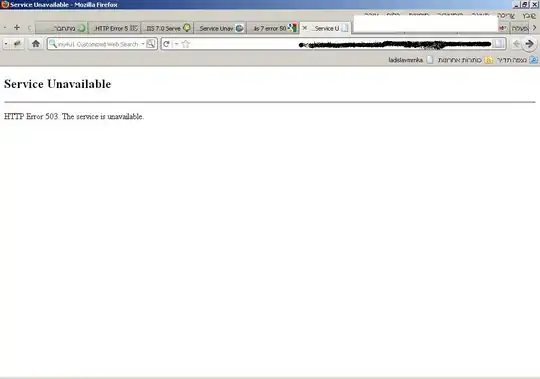
Try to read my own emails (without success):
Try to read somebody else's emails (the user was invited to access the app as a guest, but still, no success):
I don't understand why I can't read Messages but I can read Users. It seems the permissions were completely ignored (I confirmed that I don't need any permission to read the users).
UPDATE
This is my tenant name:
These are the users added to the tenant:
Important: I don't own an office 365 subscription in my Azure AD. All these emails belong to a different AD.
The previous question "The tenant for tenant guid does not exist" even though user is listed on users endpoint? is similar to mine but I believe this is not a duplicate as my problem is slightly different and the proposed solution uses OAuth1 (I am using OAuth2).