I want to be able to call the Azure rest APIs for creating/reading resources like Container instances, Container registries and storage accounts.
In my Azure AD, I registered an app for my application and got clientID, secret, and tenantId.
I have called the following API to get the token:
https://login.microsoftonline.com/{{tenantId}}/oauth2/token
with
resource, client_id, client_secret and grant_type
as body parameters in the POST request
The token I receive from here is not working fine. I am getting the following error:
{
"error": {
"code": "AuthorizationFailed",
"message": "The client 'ff70fcft-21ub-4a7f-8h20-3f405c5d17e0' with object id 'ff70fcff-22bb-4a7f-9f20-3f405c1e17e0' does not have authorization to perform action 'Microsoft.ContainerInstance/containerGroups/read' over scope '/subscriptions/afb6001a-XXXX-4c39-XXXX-9706012c30ba/resourceGroups/app2/providers/Microsoft.ContainerInstance/containerGroups/app2' or the scope is invalid. If access was recently granted, please refresh your credentials."
}
}
However, When I copy the access token from Browser's Network tab, it works fine.
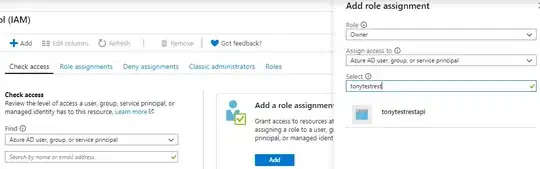
I believe that something is not right with app-registration because it feel app and my resources are currently disconnected.
Can anyone please help me out in this?