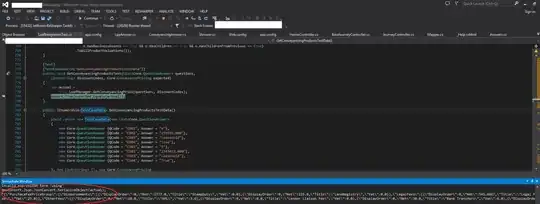
Is it possible to create the key when the azure key vault creation?
As juunas said, you need to make a separate call to achieve what you want.
I test it with the following code, it works correctly on my side. The resourceUri is https://vault.azure.net. For more details, you could refer to this SO thread.
In Key vault channel, you need to Add policies to your registered application or user. And in Access Control you need to add permission to your registered application or user.

var appId = "0000000000000000000000000000000";
var secretKey = "******************************************";
var tenantId = "0000000000000000000000000000000";
var context = new AuthenticationContext("https://login.windows.net/" + tenantId);
ClientCredential clientCredential = new ClientCredential(appId, secretKey);
var tokenResponse = context.AcquireTokenAsync("https://vault.azure.net", clientCredential).Result;
var accessToken = tokenResponse.AccessToken;
using (var client = new HttpClient())
{
client.DefaultRequestHeaders.Add("Authorization", "Bearer " + accessToken);
var requestURl = "https://xxxxxx.vault.azure.net/keys/xxxx/create?api-version=2016-10-01";
string body = "{\"kty\": \"RSA\"}";
var stringContent = new StringContent(body, Encoding.UTF8, "application/json");
var response = client.PostAsync(requestURl, stringContent).Result;
}