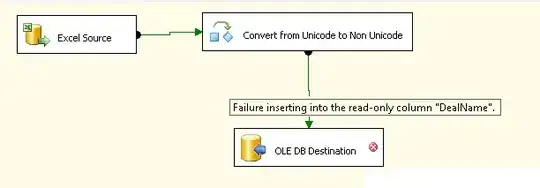
To get the authentication token for cross account permission, I will assume that you have a role to assume or you can view this tutorial how it works and how to get one.
In the tutorial above you can see a step assume role which has this command
aws sts assume-role --role-arn "arn:aws:iam::123456789012:role/example-role" --role-session-name AWSCLI-Session
the response of this command will be similar to
{
"AssumedRoleUser": {
"AssumedRoleId": "asdfa:AWSCLI-Session",
"Arn": "something"
},
"Credentials": {
"SecretAccessKey": "key",
"SessionToken": "token",
"AccessKeyId": "key"
}
}
As shown in the @jaccus answer you can use the following value and send the request via postman
- SecretAccessKey
- SessionToken
- AccessKeyId