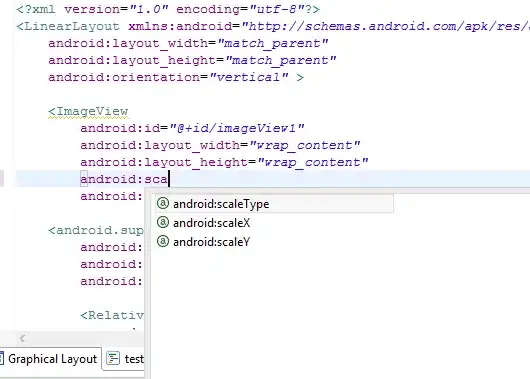
This is my WS-Security configuration with SoapUI
Server Keystore - contains server's private key + server's public key + Client's public key
Client Keystore - contains client's private key + client's public key + server's public key
2.WS-Security Configuration – Keystore
Source: path to client keystore
Password - client keystore password
and
Source: path to server keystore
Password - server keystore password
- Outgoing WS-Security Configuration
*Encryption
Keystore - server keystore
Alias - alias of server's public key
Password - Empty (no password required for public key)
Key Identifier Type - X.509
Parts - Name:Body, Namespace:http://schemas.xmlsoap.org/soap/envelope/, Encode:Content
*Signature
Keystore - client keystore
Alias - alias of client's private key
Password - password of client's private key
Key Identifier Type - X.509
Parts - Name:Body, Namespace:http://schemas.xmlsoap.org/soap/envelope/, Encode:Element
Ingoing WS-Security Configuration
Decrypt Keystore - client keystore
Signature Keystore - server keystore
Password - password of client's private key
- Applying the ws-security
- But the following exception is thrown:
19:17:35,494 WARNING [org.apache.cxf.phase.PhaseInterceptorChain] (default task-3) Interceptor for {http://soap.aaa.com/}HelloWorldService has thrown exception, unwinding now: org.apache.cxf.binding.soap.SoapFault: A security error was encountered when verifying the message
at org.apache.cxf.ws.security.wss4j.WSS4JUtils.createSoapFault(WSS4JUtils.java:216)
at org.apache.cxf.ws.security.wss4j.WSS4JInInterceptor.handleMessageInternal(WSS4JInInterceptor.java:329)
at org.apache.cxf.ws.security.wss4j.WSS4JInInterceptor.handleMessage(WSS4JInInterceptor.java:184)
at org.apache.cxf.ws.security.wss4j.PolicyBasedWSS4JInInterceptor.handleMessage(PolicyBasedWSS4JInInterceptor.java:79)
at org.apache.cxf.ws.security.wss4j.PolicyBasedWSS4JInInterceptor.handleMessage(PolicyBasedWSS4JInInterceptor.java:66)
at org.apache.cxf.phase.PhaseInterceptorChain.doIntercept(PhaseInterceptorChain.java:308)
at org.apache.cxf.transport.ChainInitiationObserver.onMessage(ChainInitiationObserver.java:121)
at org.apache.cxf.transport.http.AbstractHTTPDestination.invoke(AbstractHTTPDestination.java:251)
at org.jboss.wsf.stack.cxf.RequestHandlerImpl.handleHttpRequest(RequestHandlerImpl.java:108)
at org.jboss.wsf.stack.cxf.transport.ServletHelper.callRequestHandler(ServletHelper.java:134)
at org.jboss.wsf.stack.cxf.CXFServletExt.invoke(CXFServletExt.java:88)
at org.apache.cxf.transport.servlet.AbstractHTTPServlet.handleRequest(AbstractHTTPServlet.java:293)
at org.apache.cxf.transport.servlet.AbstractHTTPServlet.doPost(AbstractHTTPServlet.java:212)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:707)
at org.jboss.wsf.stack.cxf.CXFServletExt.service(CXFServletExt.java:136)
at org.jboss.wsf.spi.deployment.WSFServlet.service(WSFServlet.java:140)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:790)
at io.undertow.servlet.handlers.ServletHandler.handleRequest(ServletHandler.java:85)
at io.undertow.servlet.handlers.security.ServletSecurityRoleHandler.handleRequest(ServletSecurityRoleHandler.java:62)
at io.undertow.servlet.handlers.ServletDispatchingHandler.handleRequest(ServletDispatchingHandler.java:36)
at org.wildfly.extension.undertow.security.SecurityContextAssociationHandler.handleRequest(SecurityContextAssociationHandler.java:78)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.servlet.handlers.security.SSLInformationAssociationHandler.handleRequest(SSLInformationAssociationHandler.java:131)
at io.undertow.servlet.handlers.security.ServletAuthenticationCallHandler.handleRequest(ServletAuthenticationCallHandler.java:57)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.security.handlers.AbstractConfidentialityHandler.handleRequest(AbstractConfidentialityHandler.java:46)
at io.undertow.servlet.handlers.security.ServletConfidentialityConstraintHandler.handleRequest(ServletConfidentialityConstraintHandler.java:64)
at io.undertow.security.handlers.AuthenticationMechanismsHandler.handleRequest(AuthenticationMechanismsHandler.java:60)
at io.undertow.servlet.handlers.security.CachedAuthenticatedSessionHandler.handleRequest(CachedAuthenticatedSessionHandler.java:77)
at io.undertow.security.handlers.NotificationReceiverHandler.handleRequest(NotificationReceiverHandler.java:50)
at io.undertow.security.handlers.AbstractSecurityContextAssociationHandler.handleRequest(AbstractSecurityContextAssociationHandler.java:43)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at org.wildfly.extension.undertow.security.jacc.JACCContextIdHandler.handleRequest(JACCContextIdHandler.java:61)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.server.handlers.PredicateHandler.handleRequest(PredicateHandler.java:43)
at io.undertow.servlet.handlers.ServletInitialHandler.handleFirstRequest(ServletInitialHandler.java:284)
at io.undertow.servlet.handlers.ServletInitialHandler.dispatchRequest(ServletInitialHandler.java:263)
at io.undertow.servlet.handlers.ServletInitialHandler.access$000(ServletInitialHandler.java:81)
at io.undertow.servlet.handlers.ServletInitialHandler$1.handleRequest(ServletInitialHandler.java:174)
at io.undertow.server.Connectors.executeRootHandler(Connectors.java:202)
at io.undertow.server.HttpServerExchange$1.run(HttpServerExchange.java:793)
at java.util.concurrent.ThreadPoolExecutor.runWorker(Unknown Source)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(Unknown Source)
at java.lang.Thread.run(Unknown Source)
Caused by: org.apache.wss4j.common.ext.WSSecurityException: BSP:R5424: Any ENC_KEY_INFO MUST have exactly one child element
at org.apache.wss4j.common.bsp.BSPEnforcer.handleBSPRule(BSPEnforcer.java:56)
at org.apache.wss4j.dom.processor.ReferenceListProcessor.checkBSPCompliance(ReferenceListProcessor.java:231)
at org.apache.wss4j.dom.processor.ReferenceListProcessor.decryptDataRefEmbedded(ReferenceListProcessor.java:151)
at org.apache.wss4j.dom.processor.ReferenceListProcessor.handleReferenceList(ReferenceListProcessor.java:103)
at org.apache.wss4j.dom.processor.ReferenceListProcessor.handleToken(ReferenceListProcessor.java:67)
at org.apache.wss4j.dom.engine.WSSecurityEngine.processSecurityHeader(WSSecurityEngine.java:344)
at org.apache.cxf.ws.security.wss4j.WSS4JInInterceptor.handleMessageInternal(WSS4JInInterceptor.java:280)
... 42 more
And These are the raw type of soapmessage
POST http://localhost:8080/SOAPSecurityWeb/HelloWorld HTTP/1.1
Accept-Encoding: gzip,deflate
Content-Type: text/xml;charset=UTF-8
SOAPAction: ""
Content-Length: 4354
Host: localhost:8080
Connection: Keep-Alive
User-Agent: Apache-HttpClient/4.1.1 (java 1.5)
<soapenv:Envelope xmlns:soap="http://soap.aaa.com/" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header><wsse:Security xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"><xenc:ReferenceList xmlns:xenc="http://www.w3.org/2001/04/xmlenc#"><xenc:DataReference URI="#ED-762310919C4F29F7D9146737020258012"/></xenc:ReferenceList><ds:Signature Id="SIG-762310919C4F29F7D9146737020256711" xmlns:ds="http://www.w3.org/2000/09/xmldsig#"><ds:SignedInfo><ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"><ec:InclusiveNamespaces PrefixList="soap soapenv" xmlns:ec="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:CanonicalizationMethod><ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/><ds:Reference URI="#id-762310919C4F29F7D9146737020256710"><ds:Transforms><ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"><ec:InclusiveNamespaces PrefixList="soap" xmlns:ec="http://www.w3.org/2001/10/xml-exc-c14n#"/></ds:Transform></ds:Transforms><ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/><ds:DigestValue>CQMC6AlBzVr4GlcwEgCTuaLepn4=</ds:DigestValue></ds:Reference></ds:SignedInfo><ds:SignatureValue>TuzMIyUtSxayHLjfq0TGEEsVXkJdwpL+MGSwwuSQF+9J2t8brCkRvLlNGNvypsORlIPCXPwnxrYG
iFebfSFkIx2hke+Jt9/rRc6stg/iBfeVUrXPn0frOTyi3c7VNZpQIRv7+YE21XXuzxLqMNNoejb4
lDiFnc0VmnNU6GvM/WBf5FXhxr+E2amGcpYbi2yOKMe8pfsj5sRTDUWLkjt4qYU3LmnRpl3kYg8j
ZIF9CgryM5phxrTm18baYwZOWf2whdhNxkd6iEBt/+OMF+uVuW4YStxzKINaR2lSdHquFef3FheA
993frgWKXz8s63nLBLjJXXfLskqhdZdLj7s8Zg==</ds:SignatureValue><ds:KeyInfo Id="KI-762310919C4F29F7D914673702025678"><wsse:SecurityTokenReference wsu:Id="STR-762310919C4F29F7D914673702025679"><wsse:KeyIdentifier EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary" ValueType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-x509-token-profile-1.0#X509v3">MIIDazCCAlOgAwIBAgIEJaiHjTANBgkqhkiG9w0BAQsFADBmMQswCQYDVQQGEwJLUjESMBAGA1UECBMJS3lvdW5nTmFtMQ4wDAYDVQQHEwVQdXNhbjESMBAGA1UEChMJTXkgZmFtaWx5MQwwCgYDVQQLEwNERVAxETAPBgNVBAMTCEppbmEgS2ltMB4XDTE2MDUxNTA3MTIyOVoXDTE2MDgxMzA3MTIyOVowZjELMAkGA1UEBhMCS1IxEjAQBgNVBAgTCUt5b3VuZ05hbTEOMAwGA1UEBxMFUHVzYW4xEjAQBgNVBAoTCU15IGZhbWlseTEMMAoGA1UECxMDREVQMREwDwYDVQQDEwhKaW5hIEtpbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAIb7rclNqyRSJDuKBYNqO+I50Lf7AK/ccZgXePGsDVCA5QVmimQgPdvW9fILdJ13rNGyC06BexDC6lGpfhE6Bu3Arz5EkydQKKDWsa3hcY/EuyAK2blr9BAfOHz9wBaWtc3ro1p3gZBaVBPkA6q9DHJjFIHVeKjbzK0m8ipGiXpYcL4B/Nexac7W60n6dVPK5hoa5769ZI7oqN/n2DJNw8HGxbZMAjBvqegvtAkx3qGXPbdNmpEoS8Jd72Tg0KKlbmxUoG2p5ol+urSbKAeyq45+loINN1uIjcVGHvJfVCy3pQSkfaS7eXwbReFa2ok7GMywwGxamT1H6xTIYdHCdKsCAwEAAaMhMB8wHQYDVR0OBBYEFLkqHMaCP8EXbZTkaByzh9bH9vMFMA0GCSqGSIb3DQEBCwUAA4IBAQBj1Lovsj/AGirxDd6cBqTR25c9lDGB8vBlkfHxusL/L/AVYkiNKJR72GrK3PP+w0eblmfBqGYXaOeBIvW+KqOOUWiWIaSsOQUpzOUUqvvIvmdya8s8PhAcI8nYD50SdRCjUq9SXaSxZSQ9hZ87OFBQ5icXhHS4CCjZ8Jh46rZvrBL7tZbKDhVz5LwCtGgAkgq3/rcf2W6gKFYU4g1+KEB+4+57HBuPtGkbjSwaj5oFvv7+sTyJvdxvRBvTh2UEEEK1QtCMtQULGYjb4imOwHQbSM/UKtRgRVFcOnVzx34Pvib06PX0aNuW2AWEu+G/IJ4sS5KYvLujM+wxraxH1Ad1</wsse:KeyIdentifier></wsse:SecurityTokenReference></ds:KeyInfo></ds:Signature></wsse:Security></soapenv:Header>
<soapenv:Body wsu:Id="id-762310919C4F29F7D9146737020256710" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"><xenc:EncryptedData Id="ED-762310919C4F29F7D9146737020258012" Type="http://www.w3.org/2001/04/xmlenc#Content" xmlns:xenc="http://www.w3.org/2001/04/xmlenc#"><xenc:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/><ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#"/><xenc:CipherData><xenc:CipherValue>driG0+hdn4kuBUL545mLKBioB7Cm57Bm0XwyVjkBV8f0VcxPUu4OqkHtRaJYv6MIhmEDDfYiLm5Y2JaijNh7WQnAzWkhh/gfyoXJ4XzVDSOlUPZ1+C4kFgF24zmPHsLhl4oUiLWCDJ3cuAsDNRRzHSHI3T9ONYX9RbekAUwvKFspsAIbYE3YXQuNr7Ux/9GySNxIwBwnd50VvjLaqGNseeBDDAJyKrgSg2REqk9v8IJfh6ue0haLVIMF/xCIO+Qsgvwcpyd5/emSqbXkaFx+d9OCLFgKNs+sTHHy1BybfElsOIamLU9TEdD2PSVP7Frf3ESR2wOBiz0XWBiT1a/1zkjWCh72jbsFzd48x/FXywKbTlF+s5rhCqhBt6lLctlHRIxN8IpQesMNS/jFpc9A3b6dHOvOSx8y5ex4KWIK/Ms=</xenc:CipherValue></xenc:CipherData></xenc:EncryptedData></soapenv:Body>
</soapenv:Envelope>
HTTP/1.1 500 Internal Server Error
Connection: keep-alive
X-Powered-By: Undertow/1
Server: WildFly/10
Content-Type: text/xml;charset=UTF-8
Content-Length: 299
Date: Fri, 01 Jul 2016 10:50:02 GMT
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/"><soap:Body><soap:Fault><faultcode xmlns:ns1="http://ws.apache.org/wss4j">ns1:SecurityError</faultcode><faultstring>A security error was encountered when verifying the message</faultstring></soap:Fault></soap:Body></soap:Envelope>