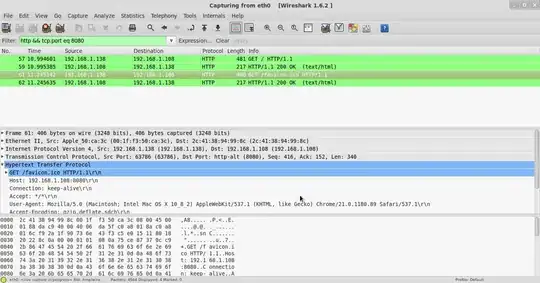
I have a .pcap packet which received to analysis malicious activity. Using Snort IDS and BarnYard2 detection I've captured 4 selectivities to BASE ( Basic Analysis and Security Engine ) which shows as Portscan Traffic 100% . four have 2 different IP address
Source : 10.214.116.188 Destination : 213.157.159.151
and
Source : 10.214.116.188 Destination : 186.160.247.133
Packet Opened with WireShark and first filter of
ip.dst==186.160.247.133
and second filter
ip.addr==213.157.159.151
I need support to help understand what kind of attack this perform and how i can learn moreover about it.
packet : https://drive.google.com/file/d/0B-dY0nxt4UZXNGZ4UE5XbmZsY1U/view?usp=sharing