I'm running Tomcat on a CentOS vm in Azure. No firewall on host. wget localhost:8080 returns a page as does the same request on private IP address. I can SSH into the server using the public IP address, but wget public_IP_address:8080 does not route to the host.
I have enabled inbound security rule for port 8080, which looks to be identical to the one that allows SSH over port 22.
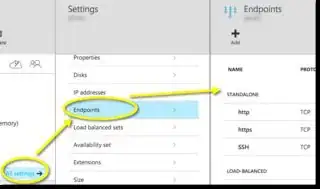
I've been researching this for hours. It seems all the articles about running Tomcat on a linux host in Azure are written with Classic Virtual Machine administration UI. They talk about specifying an endpoint, which isn't available in the modern Azure UI. I likewise see info about establishing an "ILPIP," but that seems to require powershell, which isn't on my CentOS host.
I likewise can't find anything about modifying the supposed "VIP" that's illustrated in above article.
What am I missing for enabling TCP access to my Tomcat server listening on port 8080 on my CentOS virtual machine in Azure?
Update:
Per the suggestion of @MichaelB, I installed Azure command line tools on Mac OS X.
$ azure vm show minimalfalcon
info: Executing command vm show
+ Getting virtual machines
warn: No VMs found
info: vm show command OK
In the current Portal UI, clicking 'Virtual Machines (Classic)' shows no instances. When I click 'Virtual Machines,' that's how I access all the settings for my VM. I suspect the Azure CLI tool is connecting to the classic API instead of whatever the current portal uses. And the portal isn't offering classic access to my VM.
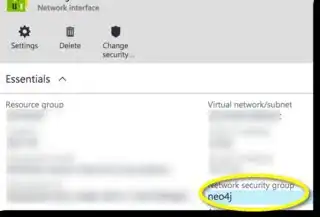
I additionally followed @MichaelB's suggestion of disabling the inbound rule for SSH in the security group. Sure enough, SSH access persisted to this VM! So, when I navigate:
Virtual machines >> minimalfalcon >> Settings >> Network interfaces >> minimalfalcon447 >> Network Security Group (minimalfalcon) >> Settings >> Inbound security rules
Those don't really control access to my Virtual Machine. See below screenshot. What hoop needs to be jumped through to apply this network security group policy to my VM? I really can't see how this isn't supposed to be applied. Any guidance appreciated!