I am writing a TCPClient class for communicating with a SSL/TLS TCP socket server in Swift, and the server is automatically generating self-signed certificates when it doesn't find or isn't able to successfully use a valid certificate. These self-signed certificates are being used as the socket server
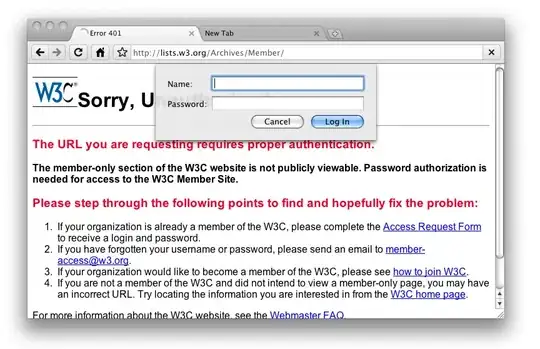
I am trying to set up an iOS app to prompt the user with a similar dialog of browsing an invalidly signed webpage when the TCP client gets an invalid SSL certificate.
Here's the dialog I want to display to users:
Here's how the TCP connection is made:
public class TCPClient: NSObject, NSStreamDelegate {
let serverAddress = "127.0.0.1"
let serverPort = 7000
private var inputStream: NSInputStream?
private var outputStream: NSOutputStream?
public func connect() {
println("connecting...")
NSStream.getStreamsToHostWithName(self.serverAddress, port: self.serverPort, inputStream: &self.inputStream, outputStream: &self.outputStream)
self.inputStream!.delegate = self
self.outputStream!.delegate = self
self.inputStream!.open()
self.outputStream!.open()
self.inputStream!.setProperty(NSStreamSocketSecurityLevelTLSv1, forKey: NSStreamSocketSecurityLevelKey)
self.outputStream!.setProperty(NSStreamSocketSecurityLevelTLSv1, forKey: NSStreamSocketSecurityLevelKey)
var buffer: [UInt8] = [0]
// buffer is a UInt8 array containing bytes of a string.
self.outputStream!.write(&buffer, maxLength: buffer.count)
}
public func stream(aStream: NSStream, handleEvent eventCode: NSStreamEvent) {
println("stream event.")
}
}
Currently I only see this when trying to connect:
connecting...
2015-09-13 19:48:25.562 AppName[] CFNetwork SSLHandshake failed (-9807)