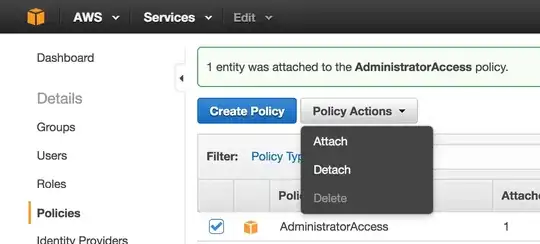
I am trying to setup AWS CLI tools and was following instructions at http://docs.aws.amazon.com/AWSEC2/latest/CommandLineReference/set-up-ec2-cli-linux.html#setting_up_ec2_command_linux
However, after following all the steps and setting up my AWS_ACCESS_KEY and AWS_SECRET_KEY, I get
$ ec2-describe-regions
Client.UnauthorizedOperation: You are not authorized to perform this operation. (Service: AmazonEC2; Status Code: 403; Error Code: UnauthorizedOperation; Request ID: 55f02cc4-2e9f-4a0a-8b55-46bcc1973f50)
I then tried regenerating new credentials, but still getting the same error. I couldn't seem to find information about anyone else having this issue. I tried passing the keys using -O and -W, but that doesn't work either.
Any idea what I might be doing wrong?