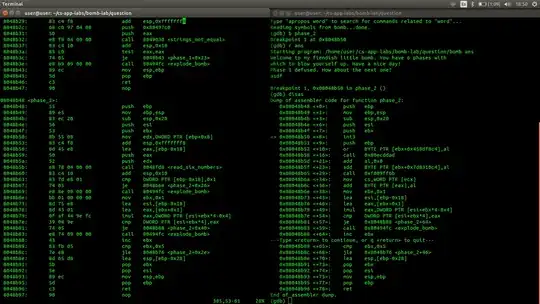
you'll need to save the image to read the instructions in the image
well, here's the problem.
I'm working on a bomblab just for killtime and I'm stuck with the issue
of different assembly code generation of objdump and gdb.
my laptop is running 64-bit Ubuntu 14.04 LTS and
I've installed 32bit glibc to work on bomblab.(since it's compiled in 32-bit env)
well, first the symbols aren't showing and I don't really get what gdb is spitting out.
Can someone explain me what's going on?