On many banking and investment websites, the site prevents users from logging in from an unrecognized computer without first answering an additional question or activating that machine. How do developers typically create this feature?
For example, here is the message that Salesforce.com gives when I connect to my account from an unrecognized machine:
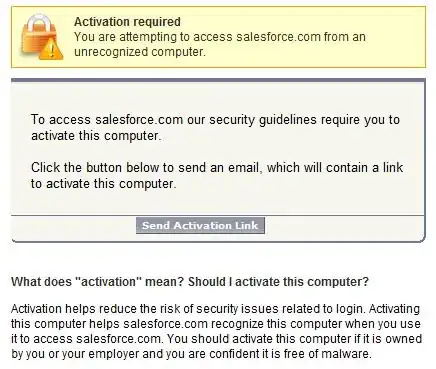
We're trying to do the same type of thing from one of our applications, but aren't sure about the best (and most secure) approach.