While developing our 64bit driver, we came to understand that every driver needs to be correctly digitally signed to install (except in Test Mode).
Recently, we stumbled over a driver (for an USB camera), that seems to be missing a valid signature. During installation, we get the red warning screen about unsigned drivers, but the device works correctly using this driver.
I have taken photos. Sorry for the wall of images, I was afraid to miss an important point, since I obviously don't understand what's going on here.
Devive Manager
Driver Properties
Driver Details
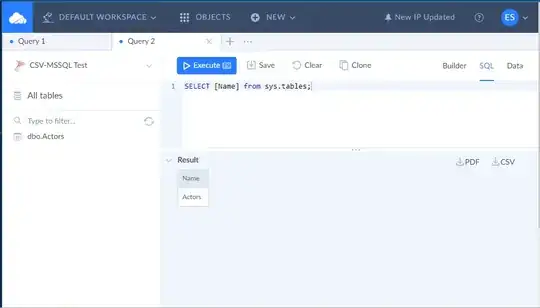
Driver Files from %system32%\DriverStore\FileRepository

Certificate Details
Test Mode was off for this (and our own driver correctly failed to load).
How did they do that? Why is Windows loading this driver? I would be grateful for some links into the documentation explaining this behaviour.
Edit:
Using the verbose CodeIntegrity log as suggested in the comments, I find nothing off. The log shows a line
Code Integrity found a file hash for the file in oem132.cat
This file exists in %system32%\catroot\some-guid and is identical to the cat file shown in the screenshot above; expired certificate included.
signtool verify /v /c .\mvBlueFOX_amd64.cat .\mvBlueFOX2.sys gives
Verifying: .\mvBlueFOX2.sys
File is signed in catalog: .\mvBlueFOX_amd64.cat
Hash of file (sha1): 19E6125B9C5F31E21EDA5DBAA5F77798F8E394C4
Signing Certificate Chain:
Issued to: Class 3 Public Primary Certification Authority
Issued by: Class 3 Public Primary Certification Authority
Expires: Thu Aug 03 00:59:59 2028
SHA1 hash: A1DB6393916F17E4185509400415C70240B0AE6B
Issued to: VeriSign Class 3 Code Signing 2009-2 CA
Issued by: Class 3 Public Primary Certification Authority
Expires: Tue May 21 00:59:59 2019
SHA1 hash: 12D4872BC3EF019E7E0B6F132480AE29DB5B1CA3
Issued to: MATRIX VISION GmbH
Issued by: VeriSign Class 3 Code Signing 2009-2 CA
Expires: Tue May 07 00:59:59 2013
SHA1 hash: 75859F3121E3852E2894E1A7B388CB9E68EBC237
File is not timestamped.
SignTool Error: A certificate chain processed, but terminated in a root
certificate which is not trusted by the trust provider.
Number of files successfully Verified: 0
Number of warnings: 0
Number of errors: 1