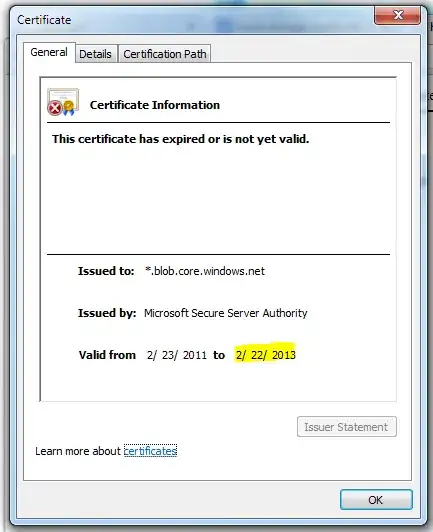
The certificate for our Azure blob storage expired today. This is not a certificate provided by us but provided by Microsoft as show in the picture below. How does one go about fixing this? I have tried searching for a solution but found nothing. Our app cannot connect to the storage as the certificate has expired and we are getting an error indicating: Could not establish trust relationship for the SSL/TLS secure channel