It's certainly possible and it has happened in a few cases.
Here's an example of this happening, as reported by media:
The FBI appears to have begun using a novel form of electronic surveillance in criminal investigations: remotely activating a mobile phone's microphone and using it to eavesdrop on nearby conversations.
—FBI taps cell phone mic as eavesdropping tool
The article also mentions its sources, which we can check:
Judge Jones
granted the application, authorizing continued interception at the
four restaurants and the installation of a listening device in
Ardito's cellular telephone. The device functioned whether the phone
was powered on or off, intercepting conversations within its range
wherever it happened to be.
—UNITED STATES of America, v. John TOMERO, et al., Defendants.
The second link points to an old NOAA page which warns:
A cellular telephone can be turned into a microphone and transmitter for the purpose of listening to conversations in the vicinity of the phone. This is done by transmitting to the cell phone a maintenance command on the control channel. This command places the cellular telephone in the "diagnostic mode." When this is done, conversations in the immediate area of the telephone can be monitored over the voice channel.
—Cellular Phones
The article has been removed by NOAA, and the link points to an USDA version.
Further on, we can find references to these bug existing back to 2004:
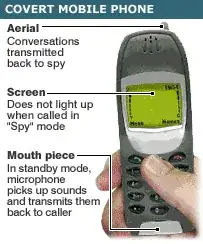
Mobile phones
According to security experts, the most common listening device remains the electronic bug.
But government agencies such as the CIA and MI5 have far more advanced systems at their disposal.
—'This goes no further...'
The BBC also reports this happening at the United Nations (with my emphasis):
But today's spies are also able to convert conventional phones into bugs without the owners' knowledge.
Experts believe this is the most likely method used to gather information in the UN building.
[...]
According to some reports, intelligence services do not even need to obtain permission from the networks to get their hands on the codes.
So provided it is switched on, a mobile sitting on the desk of a politician or businessman can act as a powerful, undetectable bug.
[...]
According to one security expert, telephone systems are often fitted with "back doors" enabling them to be activated at a later date to pick up sounds even when the receiver is down.
